This article is more than 1 year old
Bootkit ransomware baddy hops down BadRabbit hole in Japan
Spirited away...
A new strain of ransomware is apparently being used for targeted attacks in Japan.
MBR-ONI, a new bootkit ransomware, relies on modified version of a legitimate open-source disk encryption utility called DiskCryptor for its encryption routines – the same tool abused by the Bad Rabbit ransomware last week.
While ONI and the newly discovered MBR-ONI exhibit all the characteristics of ransomware, security intelligence firm Cybereason reckons the malware strains are being used as destructive wipers meant to cover up evidence of targeted attacks against Japanese companies.
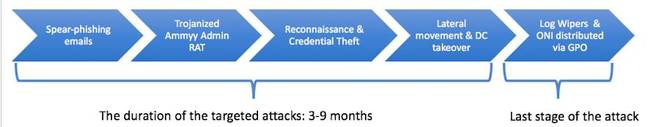
We suspect that the ONI ransomware might have been used as wipers to cover up an elaborate hacking operation. These targeted attacks lasted between three to nine months and all ended with an attempt to encrypt hundreds of machines at once.
Forensic artifacts found on the compromised machines shows that the attackers made a significant attempt to cover their operation.
MBR-ONI is being used in conjunction with ONI, an earlier strain of ransomware, in the same string of attacks, according to Cybereason. As well as being deployed together, both strains of nasty share the "same email address", claimed researchers. The use of two strains of ransomware in the same attack when one would have achieved the same ends remains a puzzler for both Cybereason and other interested observers.
While the latest attack is specific to Japan, targeted attacks involving ransomware/wipers have been on the rise across the world in recent years. High profile examples include the Shamoon attacks against Saudi Aramco, RasGas and other targets.
The malware in the latest Japanese attacks appears in the guise of spear-phishing emails carrying weaponised Office documents, ultimately designed to drop the Ammyy Admin RAT. Malware payloads were carried by password-protected zip files in tainted emails. Prospective marks who opened a zip file were induced into enabling macros, allowing a VBScript that downloaded and executed the RAT.
Using Ammyy Admin and other hacking tools, the attackers mapped out the internal networks, harvested credentials and moved laterally, ultimately compromising critical assets, including the domain controller (DC) before gaining full control of targeted networks. Ammyy Admin is a legitimate remote administration tool – albeit one that's frequently abuse by black-hat hackers.
Cybereason said it suspects the hackers used the NSA-leaked EternalBlue exploit in conjunction with other tools to spread throughout the network. Data corruption and log wiping associated with successful attacks mean there is no proof on this point, however Cybereason found that the MS17-010 security update (released in March 2017) was not installed on the compromised machines. In addition, SMBv1 was still enabled across the compromised environments.
Hackers behind the attacks are operating a scorched earth policy. In addition to the ransomware, the attackers used a batch file whose purpose was to thoroughly clear Windows’ event logs (over 460 logs). This action was is applied in the later stages of an attack through a rogue group policy. In addition, the ONI binary file was also copied from the Domain Controller and executed, encrypting a large array of files.
While ONI was used against most of the computers on targeted networks, MBR-ONI was used on only a handful of endpoints, according to Cybereason. These endpoints were critical assets (Active Directory server, file servers, etc).
The Japanese attacks ran for at least nine months between December 2016 (or possibly earlier) and September 2017.
ONI seems to share code with GlobeImposter ransomware variants, and some routines are even identical, according to Cybereason. MBR-ONI borrows a large portion of its code from DiskCryptor. The attack shows that, with some code modification, a legitimate disk encryption utility can turn into ransomware or even a destructive wiper.
"ONI and MBR-ONI served a purpose closer to a wiper than that of a ransomware - covering up an ongoing hacking operation by destruction of data," Cybereason concluded.
Botnote
ONI received its name based on the file extension that it appends to the files it encrypts. The name ONI can mean “devil” in Japanese (鬼), and it also appears in the email address found in its ransom note. “Oninoy0ru” translates into “Night of the Devil” in Japanese (鬼の夜). Cybereason observed other versions of ONI’s ransom note that contained other email addresses whose username also included the string “ONI”.