This article is more than 1 year old
US reveals 'Target' pic of Conti man with $10m reward offer
Fashion Police chipping in on the bounty related to costliest strain of ransomware on record
The US government is putting a face on a claimed member of the infamous Conti ransomware group as part of a $10 million reward for information about five of the gang's crew.
The State Department announced the reward via the Rewards for Justice program's Twitter account, saying it is looking for information about cybercriminals associated with Conti, Wizard Spider, or Trickbot. Wizard Spider in May was identified as the Russia-linked group behind Conti and Ryuk (which rebranded as Conti in 2020), as well as the Trickbot botnet.
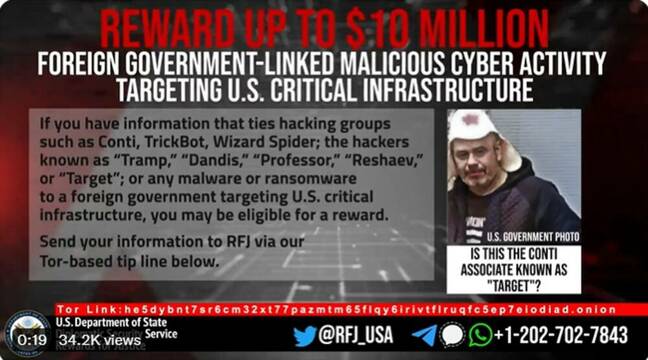
The reward notice included the aliases of the alleged attackers – "Tramp," "Dandis," "Professor,"Reshaev," and "Target" – and came with a photo of a man and a message underneath it that said, "Is this the Conti associate known as 'Target'?"
It's the first time the US government has released a photo of a suspect allegedly connected with Conti, although suspected members of other criminal gangs have been pictured.
"The US Government reveals the face of a Conti associate for the first time!" the Rewards for Justice (which offers counterterrorism rewards for the US government) tweet said. "We're trying to put a name with the face! To the guy in the photo: Imagine how many cool hats you could buy with $10 million dollars!"
US agencies have been putting a lot of money behind its efforts to dismantle the Conti operation and find the people behind it. In May, the State Department announced a reward of up to $15 million for information about the top leaders behind Conti and individuals that had participated in attacks using a variant of its malware.
At the time, the government agency said Conti was the costliest strain of ransomware on record, saying that as of January, there were more than 1,000 victims of attacks that involved Conti. Payouts from those attacks surpassed $150 million - which adds up to a huge stack of investment funds for future criminal operations.
The Conti group was behind a string of high-profile attacks, including one last year on Ireland's government healthcare system in which it demanded $20 million in ransom. The country refused to pay and sorted out the issue, while thousands of people suffered from the attack.
Conti also launched operations in the US, taking aim at law enforcement agencies, city and towns, and emergency medical services in states like Oklahoma and Florida. It also attacked the government of Costa Rica in April, disrupting the country's customs and tax platforms and damaging foreign trade.
Conti runs as a ransomware-as-a-service (RaaS) operation, developing and refining the code for other cybercriminals to pay for and use in their attacks. Like other ransomware operators, it also has adopted extortion as part of its methods, stealing data and threatening to release it publicly if the ransom isn't paid.
However, Conti as a brand has been dismantled. Pressure from government agencies – including the $15 million reward offered by the State Department – and the data leak about the group following its vocal support of Russia and its unprovoked invasion of Ukraine in February contributed to the collapse of the Conti name.
That said, group members have been tracked to other ransomware operations, including Karakurt, a gang that the FBI, CISA, and the US Treasury warned about in June, which has demanded ransoms as high as $13 million and also threaten to publicly release stolen data if the extortion demand wasn't met. ®

