This article is more than 1 year old
Tupperware-dot-com has a live credit card skimmer on its payment page, warns Malwarebytes
Branded lunchbox biz didn't answer for 5 days, alleges infosec firm
Updated Tupperware, maker of the plastic food containers beloved of the Western middle classes, has an active and ongoing malware infection on its website that steals credit card data and passes it to criminals.
Infosec firm Malwarebytes, which made the discovery, has gone public with its findings today after alleging Tupperware ignored attempts to alert it and to get the malware removed from its payment processing pages.
"On March 20, Malwarebytes identified a targeted cyberattack against household brand Tupperware and its associated websites that is still active today. We attempted to alert Tupperware immediately after our discovery, but none of our calls or emails were answered," said Malwarebyes in a statement.
The ruse works through a rogue PNG image file having been planted by criminals who found a way into Tupperware's website. Using steganography techniques to hide malicious code inside the image file to evade detection, the criminals loaded the near-silent exploit on Tupperware-dot-com around 9 March.
Malwarebytes' Jerome Segura told The Register: "We understand that businesses have been disrupted in light of the coronavirus crisis, and that employees are working remotely, which accounts for delays. Our decision to go public is to ensure that the problem is being looked at in a timely manner to protect online shoppers." He added that Malwarebytes also alerted mega card payment org Visa in its efforts to get the compromised site cleansed.
Around a million people a month visit Tupperware-dot-com, according to public web traffic data.
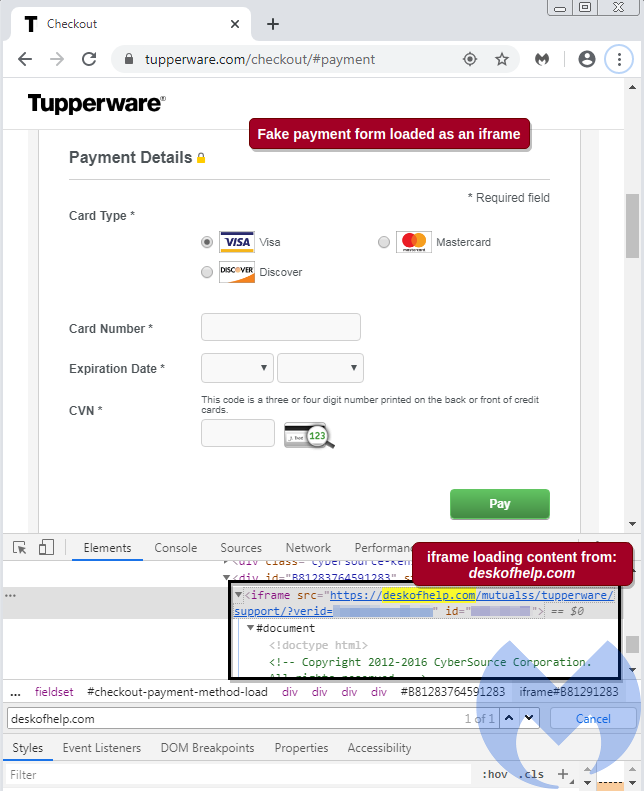
According to Malwarebytes, Tupperware.com, the plastic box purveyor's own website, was compromised by malicious persons who reprogrammed the site to launch a fake payment details iframe.
That iframe pulled its content from deskofhelp[dot]com, which infosec researchers found to be "registered to elbadtoy@yandex[.]ru, an email address with Russian provider Yandex." They po-facedly noted: "This seems at odds for a payment form on a US-branded website."
Using the iframe to pay for your boxes of goodness instead puts your payment data through a credit card skimmer, via a cunningly-disguised fake session timeout page that lets the criminals reload the correct payment page. The payment goes through on the second attempt, your data is beamed to the crims, and nobody's the wiser until your bank account suddenly empties or your credit card slams into its upper limits.
Most disturbing is that the URL for the fake payment page checks out against usual consumer-level defences of checking you really are on tupperware.com and the little HTTPS padlock shows up in the browser address bar.
The Register has asked Tupperware for comment. ®
Updated at 0915 on 26 March 2020 to add:
The plastic container maker got in touch to say: "Tupperware recently became aware of a potential security incident involving unauthorized code on our U.S. and Canadian ecommerce sites. As a result, we promptly launched an investigation, took steps to remove the unauthorized code, and a leading data security forensics firm was engaged to assist in the investigation. We also contacted law enforcement.
"Our investigation is continuing and it is too early to provide further details. We anticipate providing all necessary notifications as we get further clarity about the specific timeframes and orders that may have been involved. We want to assure our customers that protecting their information is our top priority, and we will continue to work vigilantly to pursue this matter quickly to resolution."