This article is more than 1 year old
Cloud nine to cloud nein: Google beefs up punters' data encryption to fend off cyber-thieves
Just don't forget where you put your keys and you'll be fine
Google is taking new steps to ensure the volumes of data it stores for businesses are properly protected.
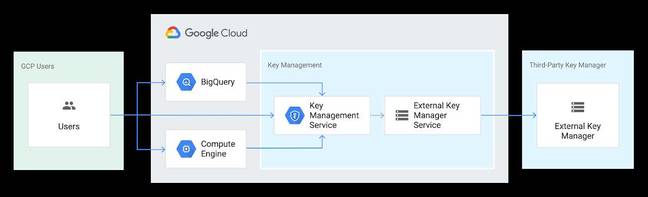
The ad-slinging network is introducing new security features to its cloud platform, including "Key Access Justification," now in alpha, which lets customers approve or deny every request for the key that decrypts their data. This can be combined with an External Key Manager feature that lets you store the keys in a third-party key management system outside Google's infrastructure.
Key Access Justifications was announced at Google Cloud Next, under way in the cavernous wastelands of London’s Excel centre. It is early days, applying only to the BigQuery data warehouse service, and Compute Engine VMs with persistent disks, and on offer only to “a select number of External Key Manager enterprise customers”, according to the announcement.
External Key Manager is in beta, otherwise keys will be stored in Google’s Cloud KMS in the same region where the resource is deployed.
“Key Access Justification works with the external key manager and provides a reason each time the key is accessed and we request to decrypt your data," said Google’s Veep of engineering, security and trust Suzanne Frey.
"This allows you do decide whether to approve or deny this request. You can deny us access for any reason. This is a level of control not available through any other cloud provider,” she claimed.
Normally access would be granted or denied by policies rather than by human interaction. There are circumstances though where you might intervene, such as when you want Google’s help to debug a problem.
“You can require us to ask you permission before anybody does anything. And when you grant us permission, we give you an audit record of every operation our operators are conducting so you can see exactly what they are doing and when,” promised GCP CEO Thomas Kurian.
When in Rome - or London
Google Next London is intended as a European event, and the company must be aware of the beady eye of the EU regulators on its compliance efforts.
“We’re introducing a number of commitments to you, our European customers,” said Kurian. “It allows you, first of all, to store your data in Europe. Not just the primary copy but all copies of data … you can also constrain us to ensure that users and administrators supporting your systems are only doing so from within Europe.” Along with Key Access Justifications, “it’s designed to meet the strictest regulatory requirements here in Europe,” he said.
The biz is keen to differentiate between its GCP services and the advertising business which dominates other parts of Google. “We do not sell ads in our cloud enterprise services,” said Frey. She also promised that “We don’t have any back doors for any government”.
On the security theme, the cloud giant also highlighted Event Threat Protection, in beta, which scans logs in search of “malware, cryptomining and unauthorized access to GCP resources”, and Security Health Analytics, also a pre-release, which scans a customer’s GCP services twice daily and feeds the results through to a dashboard called the Security Command Center.
There is also a new feature in G Suite, called App Access Control, which changes the way admins control how third-party applications access G Suite data. The existing permissions API is being replaced by an OAuth2-based system which lets you manage what data is accessed and which users have permission to use each app.
Google further announced general availability of the Advanced Protection Program for G Suite, which lets users enrol for multi-factor authentication using hardware security keys. Frey explained that it is “designed to protect executives and IT admins who face increased risk of attacks … Since we’ve implemented security keys at Google, we’ve had no reported or detected hijacking of accounts where security keys were enabled.”
The flurry of announcements amounts to a big push towards persuading customers that GCP is a safe and compliant platform for enterprise data. ®