This article is more than 1 year old
What can $10 stretch to these days? Lunch... or access to international airport security systems
Dark web does roaring trade in Remote Desktop Protocol hacks
Dark web shops are selling access to computers on corporate networks for less than the cost of a short cab ride.
Security researchers at McAfee have uncovered a network of so-called Remote Desktop Protocol (RDP) shops on the dark web which sell access to compromised IT systems, sometimes for as little as $10 a pop – which includes "access linked to security and building automation systems of a major international airport".
RDP is a proprietary Microsoft protocol, that allows a user to access another computer through a graphical interface, a powerful tool for sysadmins. The tech can also be abused by hackers, hence the growing trade in illicit login credentials. RDP access can be used by crooks to control remote systems and abuse them as jump boxes to commit other crimes.
RDP access can be used as an entry point to send spam, create false security alerts, steal data and credentials, mine cryptocurrencies, and more.
During the recent Samsam ransomware campaign against several US institutions, compromised RDP access was used to carry out the attack, which led to ransom demands of as much as $60,000.
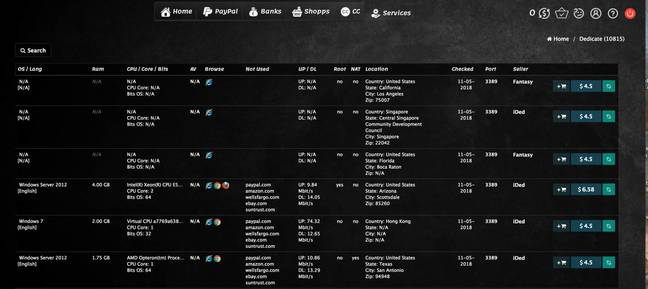
These RDP shops are growing in size and abundance on the dark web. According to McAfee, the sizes of the inventory of compromised infrastructures hawked online ranges from 15 to more than 40,000 RDP connections. The largest active shop covered by the study was held by Ultimate Anonymity Service (UAS), a Russian business.
The advertised systems ranged from Windows XP through to Windows 10. Windows 2008 and 2012 Server were the most abundant systems, with around 11,000 and 6,500, respectively, for sale. Prices ranged from around $3 for a simple configuration to $19 for a high-bandwidth system that offered access with administrator rights, McAfee said.
The same RDP machines are sometimes sold at different shops, indicating the use of resellers as part of a sophisticated underground market. In addition to selling RDP, some of these illicit outlets offer a "lively trade in social security numbers, credit card data, and logins to online shops".
McAfee came across multiple government systems being sold worldwide and dozens of connections linked to healthcare institutions, from hospitals and nursing homes to suppliers of medical equipment.
Blackpass.bz, one of the most popular RDP shops thanks to the wide range of services it offers. Click to enlarge
Attackers simply scan the internet for systems that accept RDP connections and launch a brute-force attack with popular tools such as Hydra, NLBrute or RDP Forcer to gain access. These tools combine password dictionaries with credentials leaked through data breaches.
McAfee offered tips on basic RDP security measures: enterprises should be using complex passwords and two-factor authentication to ward off brute-force RDP attacks. In addition, sysadmins should consider blocking RDP connections over the open internet. Locking out users and blocking IPs that have too many failed login attempts is another possible defence against brute-force RDP attacks. ®
![Monero mining via RDP advertised on a cybercriminal forum Monero mining via RDP ad [source: McAfee blog post screenshot]](https://regmedia.co.uk/2018/07/12/monero_mining_rdp.jpg?x=648&y=270&infer_y=1)
