This article is more than 1 year old
DVLA denies driving licence processing site is a security 'car crash'
PCI compliance? Yep, we've heard of it too
A UK government agency has disputed complaints from security pros that its website involved in the processing of driving licence applications is insecure and otherwise unfit for purpose.
Reader Andy, who asked to remain anonymous, alerted us to what he described as a "disgraceful web server configuration" at https://motoring.direct.gov.uk, a Driver and Vehicle Licensing Agency website involved in the processing of UK driving licence renewals.
Essentially, the site's HTTPS certificate and server settings for encrypting traffic, and ergo people's personal information while in transit over the internet, fall short of expectations. The weaknesses could be exploited by snoops on networks to peer at Brits' sensitive info.
"The website only handles pretty much all of your official IDs and your card numbers (certainly when you apply for a Government Gateway ID too) and is your online way to renewing your driving license," said Andy, a CISSP-qualified infosec manager. "Lord knows why it's not been spotted yet by them. Firefox won't even allow a connection without putting an exception in."
Driving licence renewal
Internet Explorer and Chrome browsers allow netizens to connect to the site as things stand, but Firefox does not without overriding a warning because the SSL/TLS security certificate chain for the DVLA site is incomplete.
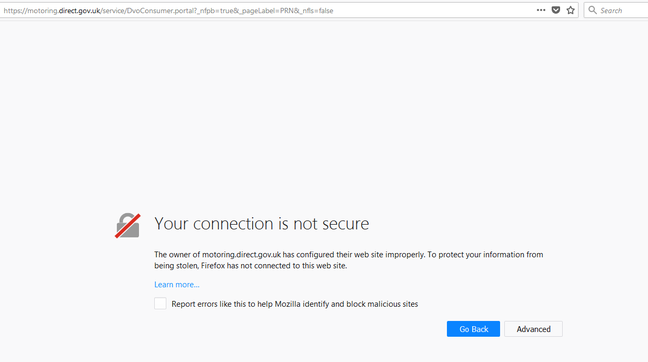
DVLA site access security warning
"Anyone that needs to apply for a driving licence renewal will end up there. I was helping out my partner doing this very deed, when we came across the mess," Andy added.
The Register invited web security expert Paul Moore to look at the DVLA site. Moore expressed disappointment bordering on disgust at what he found in the process.
Moore vented via Twitter: "Insecure ciphers, the certificate isn't installed correctly, no security headers whatsoever and you're not PCI compliant!"
In response to queries from El Reg, the DVLA sent a statement denying accusations that its website had not followed industry best practice for secure communications:
The security certificates of all of our websites meet industry standards and we use recognised industry best practice methods to ensure that all our URLs are secure. The security of our customers' data is always paramount and we constantly review our websites to ensure they are fit for purpose.
The SSL Labs rating of the site had improved to a "B" by Tuesday, February 6 after achieving only a failing (F) grade as recently as the day before. Web security experts remained unimpressed, arguing there was still work to be done.
"The certificate still isn't installed correctly and there are still no security headers," Moore told El Reg.
Our tipster, Andy, echoed this point and added that as of Thursday late afternoon he was unable to access the site using either FireFox or a Samsung S7 browser.
"The [DVLA's] boilerplate response whilst in one area factually correct, seems to miss the point," he said. "The certificate itself does meet industry standards. The configuration of the certificate onto their server, however, does not. The missing chain is still reporting on Qualys SSL. That is why Firefox and S7 browsers are rejecting the connection.
"I don't agree they are using the recognised industry best practice methods to secure their URLs. If they were, then Qualys would not have awarded an F rating on the basis of RC4 and 3DES insecure cipher suites still being active in the server configuration. They should have been removed as part of a hardening procedure pre-live."
Andy concluded that there was still a problem with the site despite some recent improvements. "[The] DVLA must have now done something about the incredibly insecure and weak ciphers they were previously peddling, as of today Qualys is reporting a grade B as opposed to the F they reported over the weekend.
"Better, but it still leaves the certificate chain issue, still some weak TLS1.2 ciphers, and I guess I hope they will switch off TLS1.0 soon, because it's insecure now anyway, and come 30 June that will be a PCI-DSS1 non-compliance!"
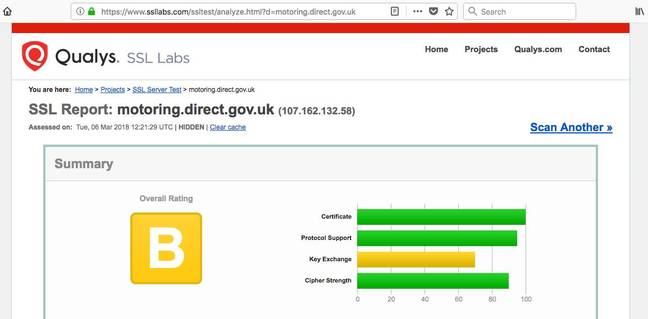
Improved SSL Labs rating for DVLA site
Insecure ciphers – perhaps enabled to ensure compatibility with older browsers – have been retired but even so problems still remain, and the site's security headers.io grade remains rock bottom.
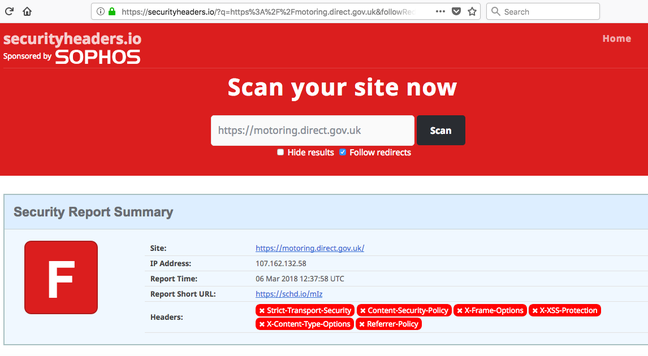
DVLA site security headers audit
Scott Helme, the researcher behind the security headers.io project, said the F grade for the DVLA site achieved with his service shows the need for remediation.
"Whilst the F grade doesn't mean they have an immediate vulnerability that could be exploited, they're not taking basic precautions to protect their users," Helme told El Reg. "If the basics aren't being covered here, where else [is] not being covered that we can't see?
"The practical effects of the findings here might not be devastating, but these tools gives us a good insight into how an organisation deals with security." ®
Bootnote
1 PCI-DSS is the credit card industry's security standard. Anyone who handles credit card payments is obliged to comply with its requirement.
