This article is more than 1 year old
Spectre shenanigans, Nork hackers upgrade, bad WD drives and more
Your weekly dose of infosec odds'n'sods
Roundup Here's a summary of this week's infosec news beyond what we've already covered in detail.
Exploits for chip blunders spook antivirus land
First up, January's Meltdown and Spectre processor security design flaws continue to haunt the IT world.
Fortinet put out an advisory on Tuesday warning 119 variants of code that exploit the CPU security cockups were detected doing the rounds last month.
The samples were collected by security lab AV-Test. Fortinet was able to confirm 83 per cent of them are proof-of-concept exploits, and couldn't find the other 17 per cent to test.
The discovery triggered a few excitable headlines, but the key thing is: this is proof-of-concept code that tests to see if it's possible to exploit Meltdown or Spectre on a machine. It's not 119 pieces of new malware that leverage the hardware flaws to steal passwords and other sensitive information from applications and the operating system.
Of course, the proof-of-concept code can be baked into software nasties to use once they've infected systems. So far, though, no known malware is abusing Meltdown or Spectre, and at least antivirus packages are getting on top of the issue by identifying code that attempts to exploit the processor faults.
"The samples will only check to see if the flaws can be exploited. The PoCs do not do any damage other than being able to capture the data in real-time via side channel attack," John Welton, a director at Fortinet, told The Register.
"All the samples we looked at were benign and based on proof of concept code.”
The patching process for Spectre on Intel and AMD-powered hardware has been fraught and full of missteps and, given the massive scale of the issue, most processors are going to remain vulnerable for some time. There's also the issue of patches causing a performance hit, to wildly varying degrees, which is dissuading some from patching when it really shouldn't.
Thankfully, there was some good news on that front. Greg Kroah-Hartman, Linux kernel maintainer for the stable branch, has been doing some benchmarking and found that upgrading to the latest version of the kernel – 4.15 – mitigates almost all of the downsides of patching the Spectre flaw.
Version 4.15 is between seven and nine per cent faster than the 4.11 build, he said. Adding a Spectre patch will slow the new build down, but because of the speed increase users should only see a very slight performance hit, around one or two per cent. Your mileage may vary.
"Although those developers who worked so hard to get that 7-9 per cent increase over the past year might not be all happy, this should help put to rest the gloom-and-doom reports," Kroah-Hartman said.
"But if you are stuck at an old kernel version (i.e. 3.10.y, 4.4.y, or 4.9.y or whatever your distro is camping on for the next decade), that's a totally different story."
Meaning systems running older Linux kernels with back-ported patches will experience a slowdown, depending on the underlying hardware and the workloads running.
Best Korea just got better
On Thursday, Adobe confirmed reports from South Korea that a nasty bug in Flash is being actively exploited to hijack victims' Windows PCs.
It was believed North Korean hackers were leveraging the flaw to spy on those investigating the shadowy dictatorship, particularly folks in the South. Now the Cisco Talos security team has found more evidence to back that up.
The Talos team has linked the exploit code to Group 123, a hacking gang sponsored by Best Korea's government. The group is known for using a remote administration tool called ROKRAT to control infiltrated systems, and it was this software that was caught exploiting the aforementioned Adobe flaw in the wild.
This, apparently, graduates the Norks from their bush league status.
"Group 123 have now joined some of the criminal elite with this latest payload of ROKRAT," the Talos team said on Friday.
"They have used an Adobe Flash zero-day which was outside of their previous capabilities – they did use exploits in previous campaigns but never a net new exploit as they have done now. This change represents a major shift in Group 123's maturity level, we can now confidentially assess Group 123 has a highly skilled, highly motivated and highly sophisticated group."
According to security researchers at FireEye, the choice of targets also fingers the attackers as coming from North Korea. The code was used against government, military, and defense industrial targets, as well as information on unification efforts and defectors.
"This is one of the North Korean actors we have been concerned about with respect to the Olympics. They could be leveraged to gather information and possibly carry out attack," said John Hultquist, director of intelligence analysis at FireEye.
"We have connected attacks to other North Korean actors, but we have not seen this actor engage in disruptive or destructive activity. Though we have not seen them execute it, we have seen these actors deploy wiper malware.”
Cyber-insurance claim spike
The rising tide of so-called business email compromises has resulted in a big rise of cyber insurance claims, according to specialist insurer Beazley.
These scams typically work like this: a miscreant, masquerading as a company executive emails an employee demanding information, such as the workforce's tax or banking details. That employee falls for the ruse and replies with archives of sensitive information. It happens a lot.
Fraudulent instruction incidents reported to Beazley quadrupled in 2017, we're told, with policyholders incurring losses ranging from a few thousand dollars up to $3m. Losses averaged out at $352,000 last year, according to claims data collected by the US-based insurer.
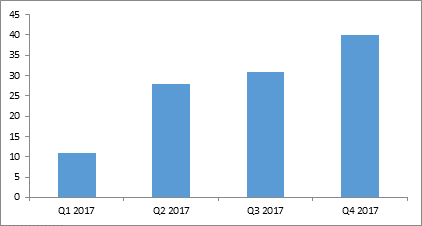
Fraudulent instruction scams growing, say cyber insurers Beazley
The top three industry sectors affected in by the scam last year were professional services (22 per cent of the total reported to Beazley), financial services (21 per cent) and retail (12 per cent), but incidents are growing across all sectors, and in particular where single large transactions, such as real-estate purchases, are involved.
Katherine Keefe, global head of Beazley Breach Response Services, commented: “Cyber-criminals are finding new ways of getting organisations to part with their hard-earned cash. In 2017 we saw fraudulent instruction emerge as a new trend which offers significant reward for the perpetrators in return for little effort, but brings potentially devastating financial consequences for the victim.”
Lock up your servers, and your drives
There's a new and particularly nasty form of ransomware in circulation that will hit less-than-stellar IT admins. Typically, ransomware is spread by spamming out attachments containing the extortion software in the hope that some not-too-bright spark will click on it. But with the latest variant of Scarab, dubbed Scarabey, its masterminds are taking a different tack.
"Instead of being distributed via Necurs malspam like the original Scarab, Scarabey was found targeting Russian users and being distributed via RDP/manual dropping on servers and systems," warned Malwarebytes Lab reverse-engineer Vhioureas on Wednesday.
"There have been a number of articles we’ve come across online that state that Scarabey has the ability to act as a backdoor, allowing remote access, and also may gather sensitive data. From our analysis, we believe this to be untrue."
Scarabey is a very nasty bit of code. Once installed and having scrambled documents, the ransomware jacks up its decryption fee over time and starts deleting some files. Just remember to keep those backups primed and ready, and verified, and offline, if you want to beat this one.
Western Digi-doh!
Backups however could be a problem – if you're using Western Digital for networked storage. Researchers at Trustwave found two serious vulnerabilities in MyCloud devices sold by WD.
The first issue was hardcoded administrator credentials found in MyCloud devices's web-based interface that could be accessed by anyone on the network – or with outside access – using the username mydlinkBRionyg. The second issue was that a logged-in normal user could inject arbitrary commands into the web control panel, and gain root access to the gadget.
Despite practicing responsible disclosure, WD has been a pain in the backside to deal with, according to Trustwave this week. The researchers informed the drive maker of the issues, sorted out a fix, and then got stone walled. They only found out the flaws had been fixed when they checked the latest WD firmware. Make sure you've got at least version 2.30.172 installed to be patched.
Gratitude – WD has heard of it. ®
