This article is more than 1 year old
Docs ran a simulation of what would happen if really nasty malware hit a city's hospitals. RIP :(
Equipment still taking too long to patch, leaving systems exposed
DerbyCon Electronic medical equipment is supposed to help humans save lives, but their lamentable security could result in considerable death, we were warned over the weekend.
Speaking at DerbyCon in Kentucky, USA, on Saturday, three medics with have a side interest in hacking gave an update on their work analyzing security flaws in medical machinery. And, reader, the results weren't good. On average, a connected device had about 1,000 exploitable CVE flaws, with some going over the 1,400 mark, it was claimed.
Not all of these flaws are remotely exploitable, but many are, "and it only takes one,” said Joshua Corman, director of the Atlantic Council's Cyber Statecraft Initiative and one of the aforementioned speakers. “Governments aren’t ready for this and hospitals certainly aren’t – 85 per cent of US hospitals don’t have any IT security staff,” he added.
Four years ago, Corman and others launched I am the Cavalry to investigate and tackle computer security that affects public safety. He gave his DerbyCon talk alongside his deputy director Beau Woods, and infosec-minded Dr Christian Dameff and Dr Jeff Tully.
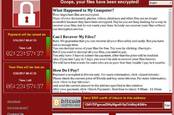
Dr Dameff highlighted the effects of the WannaCry ransomware epidemic on the UK healthcare system, and said the US had been very, very lucky not to have similar infections of malware. The main fear is a software nasty disrupting computers and network-connected equipment to the point where patients are prevented from receiving vital treatment in time.
74 countries hit by NSA-powered WannaCrypt ransomware backdoor: Emergency fixes emitted by Microsoft for WinXP+
READ MORE“When you look at stroke or heart attack victims you’ve got a very small time window to medicate and avoid further damage,” Dr Dameff explained. “A serious delay might not kill people but can certainly leave them crippled. I’m pretty confident someone died due to this [WannaCry] attack.”
The group ran a simulation exercise with the authorities in Phoenix, Arizona, that revealed alarming results. The three-day simulated cyber-disaster involved one hospital in the city being infected by destructive malware that crippled essential services, followed by other digital assaults on hospitals across the city on the second day, and then a physical attack similar to the 2013 Boston marathon bombing on day three.
To their surprise, the simulations calculated deaths would occur almost immediately on day one. With elevators and HVAC systems out, and no refrigeration for medicines, patients had to be shuttled to other medical facilities and some were not making it there alive.
By day two, doctors switched from standard to disaster triage due to the sheer volume of patients not being treated. Typically, people are triaged so that the sickest or most seriously injured get treated first, but instead doctors had to switch to prioritizing those they could realistically save and left the more seriously sick to die.
All of these deaths, in the simulation, were caused by simple hacking, usually not even requiring physical contact with the devices to exploit their weaknesses, we're told. Many older medical machines can’t be patched at all to secure them, making it pretty easy to pwn them once you're on the network or find them on the public internet, while the makers of newer systems are proving frustratingly slow to respond to security vulnerabilities.
A case in point is the St Jude pacemaker case. It took a year after a security firm pointed out the failings of the pacemaker’s firmware for the health biz to release a patch and get it approved for use, and that isn’t uncommon.
Hospitals can't even rip and replace systems and equipment to address the problem of poor device security. In general, it takes about six years to get approval from American regulators on a new medical devices and that rises to 10 if the device has to be implanted into a human. During that time, networks and kit remain potentially vulnerable to any malware that worms its way into a facility. ®
