This article is more than 1 year old
Boffins hijack bootloaders for fun and games on Android
One of these days the 'BootStomp' attack is gonna walk all over your smartmobe
University of California Santa Barbara researchers have turned up bootloader vulnerabilities across a bunch of Android chipsets from six vendors.
The team of nine researchers decided to look at a little-studied aspect Android architecture – the interaction between OS and chip at power-up. To get inside that operation, they built a tool dubbed “BootStomp” “designed to locate problematic areas where input from an attacker in control of the OS can compromise the bootloader’s execution, or its security features”.
The tool turned up exploitable bugs in Huawei, Qualcomm, MediaTek, and NVIDIA bootloaders: six new bugs, plus CVE-2014-9798 which was already known but, it turned out, was still present in Qualcomm devices (since it was a known bug, 9798 also provided a handy reference to confirm that BootStomp was working as intended).
“Some of these vulnerabilities would allow an adversary with root privileges on the Android OS to execute arbitrary code as part of the bootloader”, the group writes in its paper.
“This compromises the entire chain of trust, enabling malicious capabilities such as access to the code and storage normally restricted to TrustZone, and to perform permanent denial-of-service attacks (i.e., device bricking).”
At the bottom of the problem: the bootloader's chain of trust would ideally be the same for any chipset, but it's not – Google's left room for customisation to make life simpler for silicon vendors.
For example, in an ARM environment, chipset makers can put their own code into the process in any stage of the Trusted Boot process – and “no direction is given as to what code should be inserted at which points of the boot process”.
“Additionally, initialisation tasks cannot be too tightly coupled with the rest of the boot sequence, as peripheral hardware, such as modems, may incorporate code from different vendors and necessitate a modification of the initialisation process.”
The mobile GSM or LTE modem, for example, might be part of the system-on-a-chip (SoC) or a separate chip, and this dictates how the bootloader interacts with the chips and modem.
In other words, differences in smartphone design add decision points during boot, and could introduce vulnerabilities.
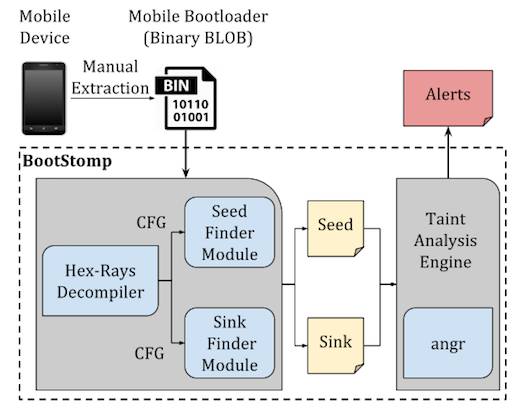
BootStomp architecture
In the Huawei bootloader, the researchers discovered a memory corruption vulnerability (exploitable to install a persistent rootkit); an arbitrary memory write (an attacker could run arbitrary code “as the bootloader itself”); and a way to root the device without user involvement.
Since a total of 38 possible bugs were discovered by BootStomp, it's fair to say nobody fared much better. Huawei and NVIDIA are named in the report as confirming the reported vulnerabilities, and the authors say only one vulnerability was denied by the vendor. ®
