This article is more than 1 year old
Cisco wireless, cloud management on this week's must-patch list
The Borg's 'This kit has Struts 2 trouble' list is also getting longer
If you've implemented Mobility Express on a Cisco 1800 access point, it needs patching against a critical authentication bypass.
Reported by Bijay Limbu Senihang of Rigo Information Technology, it's in the Web-based GUI: an attacker can send a crafted HTTP request to bypass authentication, and “perform unauthorised configuration changes or issue control commands”.
All Cisco Mobility Express 1800 systems on software prior to version 8.2.110.0 are vulnerable.
Two of Switchzilla's cloud admin systems are vulnerable to an unauthorised file retrieval bug: its Workload Automation Client Manager Server (6.3.0.116 and later); and the Tidal Enterprise Scheduler (TES) Client Manager Server (6.2.1.435 and later).
The two products have a URL validation bug that would let an attacker get any file on either system.
Cisco's Meshed Wireless LAN Controller (WLC) software has an impersonation vulnerability: an attacker can own a victim by forcing a them to connect to a rogue access point.
The following products are vulnerable if they're configured for meshed operation: Cisco 8500 Series Wireless Controller, 5500 Series Wireless Controller, 2500 Series Wireless Controller, Flex 7500 Series Wireless Controller, Virtual Wireless Controller, and Wireless Services Module 2 (WiSM2).
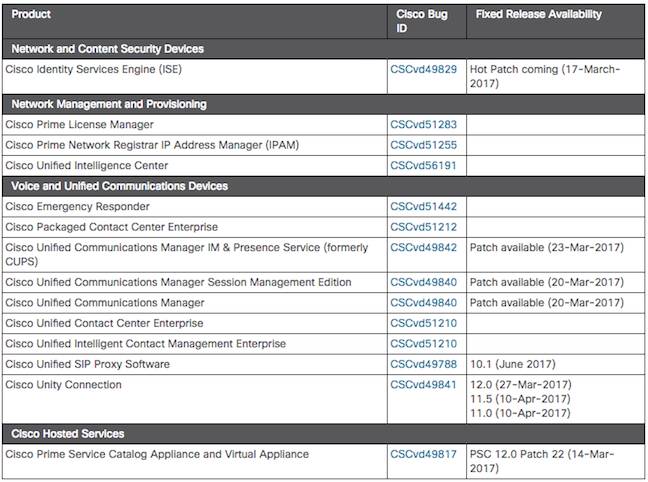
Since we're considering the security of Cisco's products, the company's also been busy working out which products are vulnerable to the Apache Struts 2 vulnerability. It's already up to Version 1.5 of its advisory, with vulnerable products listed below. ®