This article is more than 1 year old
Honeypots: Free psy-ops weapons that can protect your network before defences fail
You catch more crooks with honey than vinegar
Royal jelly
Individual free honeypot projects abound. In 2014, the Honeynet Project created the Beeswarm active honeynet, while Dell built one full of fake credentials last year. A research trio designed a honeypot to protect bitcoin wallets, while Synack engineer Nathan Yee (@nathanmyee) gifted the technology community an intelligence-laden honeypot built on Raspberry Pi.
The Honeynet Project has produced a swarm of other tools including highly interactive honeyclients, Android malware analysis tooling, and sandboxes. The European Network and Information Security Agency (ENISA) described many in its 183-page report in 2012 [PDF] authored by 11 security experts with input from dozens more. The hybrid Beeswarm honeypot is of particular note. The platform created by the Project's Johnny Vestergaard (@jkvester), who describes it as a proof-of-concept, simulates active networks and goes beyond passive honeypots that are revealed as fake on first observation of traffic. Beeswarm clients simulate communication in so-called bait sessions that are so finessed that ssh and telnet typing commands are set to average user words-per-minute speeds, all in the name of convincing attackers they are in servers.
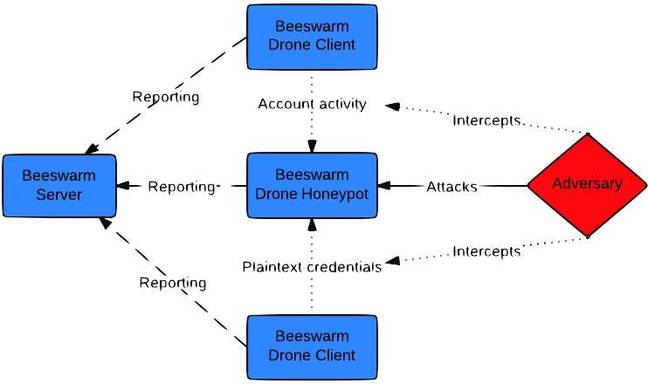
Beeswarm.
These are technologies with long-demonstrated benefits. Rist and Vestergaard offered The Register a list of what corporations investing the time into developing honeypots and honeynets can expect: "Another purpose of deploying deception technology is distraction," they say.
- Time advantage: Protect your valuable assets while the adversary struggles with the honeypot;
- Knowledge advantage: Learn how they think to adopt your defence;
- Taking control over the attackers' action: Stop reacting to them penetrating your defences and control their movement using honeypots and honeynets;
- Dilution of the attackers information: Seed your databases with false data, making it impossible for the adversary to distinguish between real data and fake data. This slows down the selling process and reduces its value;
- Increase the cost of a breach in time and resources; and
- Insight into the threat landscape: You can only protect against things you are anticipating.
