This article is more than 1 year old
AI vuln-hunter bots have seen things you people wouldn't believe
New classes of bugs found by machine-learning-powered tools
Usenix Enigma 2017 Machine-learning systems are unearthing new classes of bugs in operating systems and apps, according to bods from America's Defense Advanced Research Projects Agency (DARPA).
The exact nature of these new bug types remains under wraps, although we hear that at least one involves exploitable vulnerabilities in data queues.
Last summer, the research wing of the US military held its first Cyber Grand Challenge, a cash-prize contest to see what AI-powered software could do to shake up network security. According to two government officials speaking at this week's Usenix Enigma 2017 conference – which focuses on policy and administration – we could see the results of the research a lot sooner than some of DARPA’s other long-term research.
The cyber contest pitted seven machine-learning projects against each other in a capture-the-flag grudge match, where the computers would try to find and patch vulnerabilities in the network and attack and steal data from others.
“The cyber security systems found whole new classes of vulnerabilities,” said Lieutenant Colonel Tim Booher, program manager at DARPA’s Information Innovation Office (I2O). “Machines were very good at checking queuing areas. The ability to quickly map the entire computational process was impressive.”
The AI systems were also rather sneaky, according to John Launchbury, director of I2O. One of the competitors found a bug in operating system code used by all players, developed an exploit for the flaw, and used it to attack another competitor to steal some data. A third competitor saw what happened, figured out what the vulnerability was, and patched itself in response.
“The whole thing took just 20 minutes and that was a game changer,” he told the conference.
Cyber retrofitting and Plan X
Launchbury also detailed some of the other security research areas DARPA is investing in, including: hardening systems against attack, managing insecurity, and planning for and acting against threats.
It has eight programs in each area, and he went through the details on a few, saying that early results had been promising, particularly in retrofitting security. He detailed how 18 months ago DARPA had significant success in doing just that with a military helicopter.
The chopper had multiple points of vulnerability, Launchbury said, with old software and numerous patches. It was getting continually updated from ground systems, so the DARPA team went to work.
“We took the mission computer, we jacked it up and put a formally verified microkernel underneath it, put verified communications software on it, and then reattached the original piece of software,” he said.
They included a camera that connected to the outside world via Wi-Fi and then asked its red team to try to break into the system. They couldn’t – even when they gave the penetration testing team root access to the camera’s Linux subsystem.
Another project the DARPA boffins are beavering away on is Plan X, a scheme to provide a functional overview of the internet in the same way that satellites can show the conditions on earth or in the ocean.
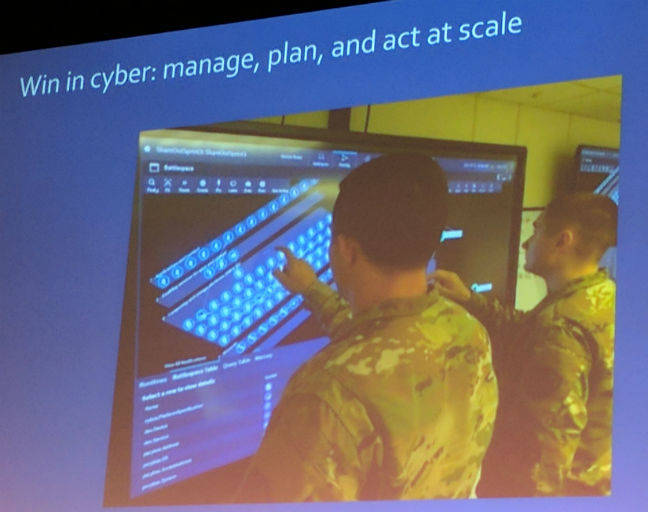
Plan X – not creepy at all
Plan X is trying to view the entire internet and map network traffic routes to see if a country’s data flows are being interfered with. The ability to observe this is the first step, he said, and they have made “huge progress” in getting a very detailed model of individual servers within the network and possibly showing the hardware and software controlling it.
This kind of detailed map will enable the researchers to view malware command and control systems, Launchbury said. He didn't elucidate on what other purposes the Department of Defense might use for such technology. ®
