This article is more than 1 year old
Yahoo! Answers used to cloak command and control networks
VXer wordsmiths demo novel stealth tricks
Two malware instances have converted numbers to words in a novel attempt to cloak the IP addresses of command and control servers.
Researchers within Palo Alto's "Unit 42" team say the malware points to location references within text written on certain public pages including Yahoo! Answers and Quora.
The unusual initiative is an effort to hid the servers from where the Confucius malware strains receive instructions and send stolen data.
Researchers reckon the malware instances are both developed by Indian-based attackers previously implicated in attacks against targets in Pakistan and neighbouring countries.
"[The malware is] using Yahoo! Answers and Quora to evade traditional mechanisms for blocking command and control domains," the research team says.
"Although we cannot link the two clusters of activity by their infrastructure, the technique used to resolve domains is unusual.
"We also believe that both clusters of activity have links to attacks with likely Indian origins, the CONFUCIUS_A attacks are linked to the use of SNEEPY/BYEBYESHELL and the CONFUCIUS_B have a loose link to Hangover."
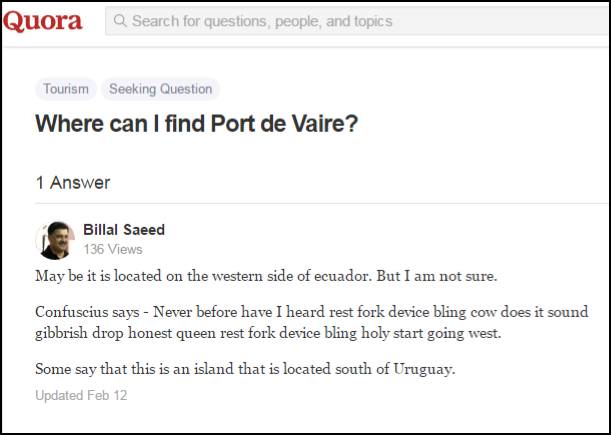
One of the Yahoo! Answers pages.
It employs various tricks including custom obfuscation techniques.
One of the two malware strains builds its DNS resolution address from the public keywords in Yahoo! and Quora posts, using the keywords to a lookup table in memory which assigns words a number.
Palo Alto released indicators of compromise and resolver URLs to help security types analyse and guard against the threats. ®
