This article is more than 1 year old
Spies rejoice! Gmail, Facebook Messenger BREACHed once again
Thrice-upgraded attack framework now 500 times faster with badass modular Rupture framework
Black Hat Asia Research pair Dimitris Karakostas and Dionysis Zindros have upgraded their attack (codenamed BREACH) that pierces the web's most common ciphers, and released a framework to help well-heeled hackers and state-sponsored spies spy on the likes of Facebook and Gmail.
At Black Hat Asia, the pair demonstrated once again how secure traffic from popular web services can be stolen, despite efforts to seal off the now three-year-old original attack vector.

Dimitris Karakostas (left) with Dionysis Zindros. Image: Darren Pauli / The Register.
The newest iteration is now more capable: attackers using the optimised BREACH (Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext) can target noisy end-points that use sluggish block ciphers, including AES 128 bit.
They say it's also 500 times faster than the original attack; browser parallelisation is sped up by a factor of six, while requests are now 16 times faster.
The original BREACH was released to much acclaim at Black Hat in 2013, and attacks the common Deflate data compression algorithm used to save bandwidth in web communications.
The original version was itself an expansion of CRIME (Compression Ratio Info-leak Made Easy), an exploit that turned compression of encrypted web requests against users.
Karakostas and Zindros (@dionyziz) of the National Technical University of Athens and the University of Athens have described their work in the paper Practical New Developments on BREACH [PDF].
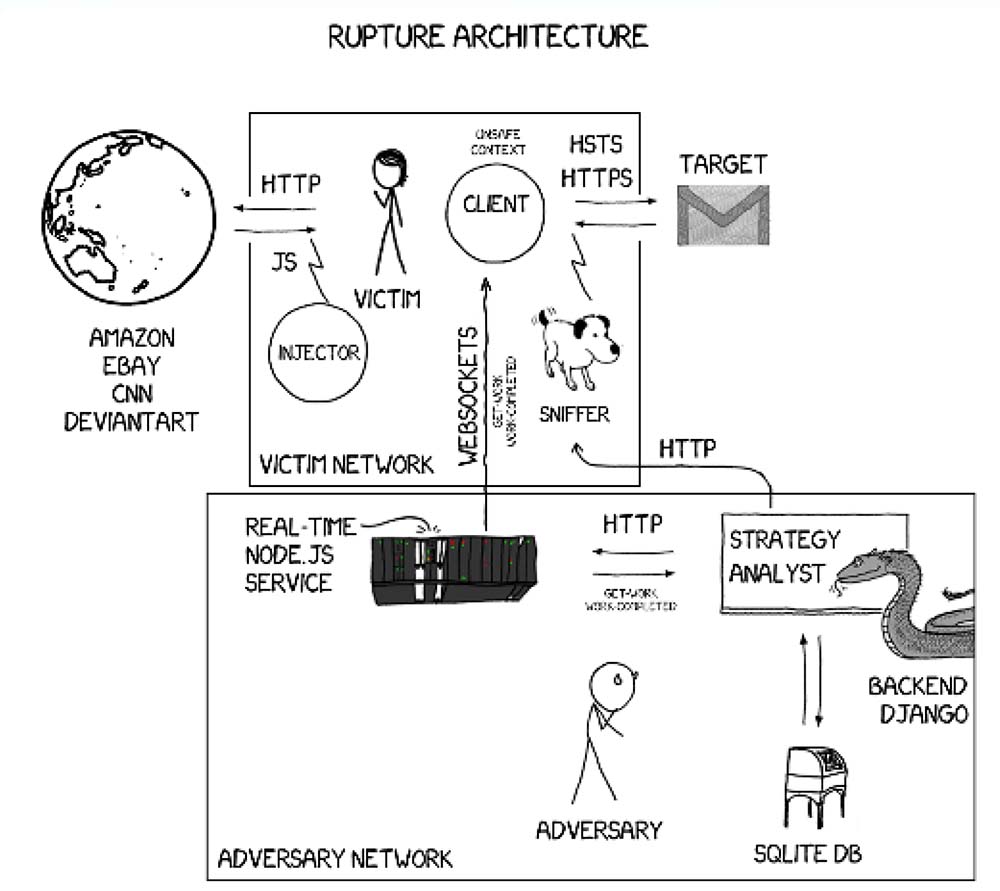
On stage, they showed security delegates how the attack could be used to read victim's Facebook messages and Gmail emails, using their "Rupture" framework, which they say makes the attack much simpler.
Launching an attack is not child's play. They told The Register it would take weeks to successfully compromise a target.
"I think with the interaction of Rupture, once people start writing target configurations for specific endpoints it is going to be much easier because it will lower the complexity of the attack," Zindros says.
"If you want to use Rupture to target an endpoint you need to study it for a bit, how it behaves, how it compresses things, if there is noise, and configure it to make it work … to steal a Gmail email or a Facebook message.
"Rupture is the implementation of our ideas, our optimisation techniques, our statistical techniques, and is not proof-of-concept - it is ready to run on real systems."
Session audio:Listen or download, slides .
The open source framework is also being developed by the team's PhD students to target the POODLE vulnerability.
The two were not out merely to ruin the day of system administrators and bathe in hacker glory; they also released simple mitigation techniques that block the attack.
First-party cookies will eliminate the problem because it removes the ability to use a targeted service as a compression oracle through which encrypted compressed secrets can be ripped out alongside plaintext data.
"The ability to mark cookies as first-party only will eliminate the existence of the oracle.
No browser has implemented the cookie scheme proposal but the duo is pushing for its penalty-free adoption. ®