This article is more than 1 year old
LastPass in 2FA lock down after 'fessing up to phishing attack
Password vault-plundering phishing bait lands on Github
Shmoocon Cloud castle for passwords LastPass has introduced mandatory sign in requirements for all new devices after security researcher Sean Cassidy dropped code allowing criminals to plunder vaults with mirror-perfect phishing attacks.
As of today, users who set two factor authentication will need to hop to their registered email accounts to approve the device they are using to sign into LastPass.
It was previously a requirement for daredevils not using two factor.
The change is a rapid move to quell online anarchy in the wake of research finding most users would likely be hosed in phishing attacks that request users enter their details including two factor authentication credentials into very legitimate-looking alerts.
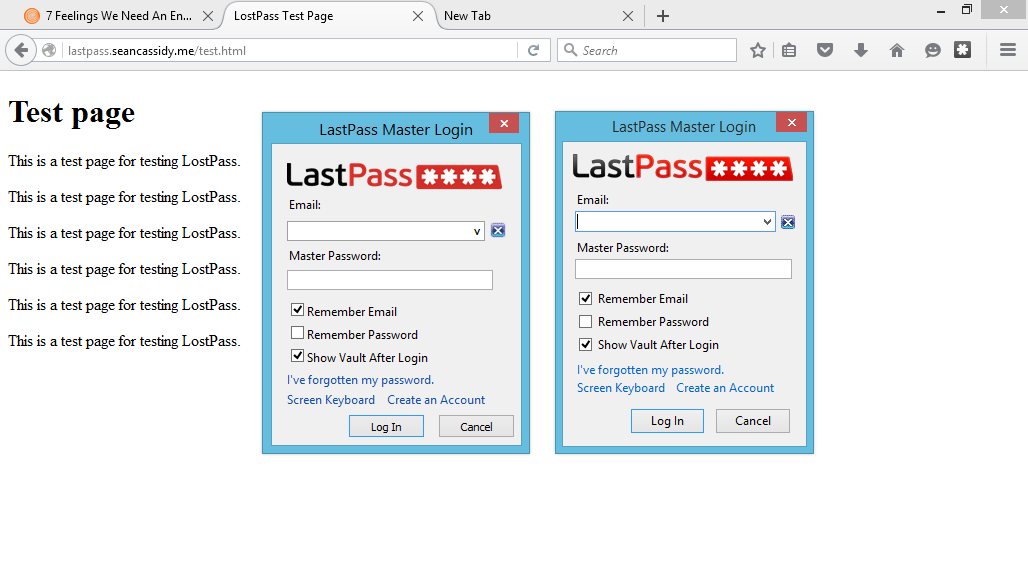
Until hours ago it meant criminals could very quickly spin up pre-fab phishing pages or simply direct users to cross-site scripting -vulnerable legitimate sites .
Criminals could make their own phishing pages targeting the new LastPass version 4 "in less than a day", Cassidy says.
"I am publishing this [phishing] tool so that companies can pen-test themselves to make an informed decision about this attack and respond appropriately."
Attackers could block warning prompts that LastPass would normally throw in the event their vault master password is entered anywhere but the official website.
LastPass acknowledged the 'LostPass' attack in December and considered a less significant phishing issue.
Cassidy (@sean_a_cassidy) , chief technology wonk of Seattle-based security outfit Praesidio, published code to Github after giving a talk at the ShmooCon conference in Washington.
He explains how attackers can create a banner -- or viewport -- to fool users into entering their credentials, and log victims out of their accounts using a known cross-site request forgery flaw open to any website.
"Unlike most phishing attacks, users won't be on their guard because this isn't supposed to be a secure website," Cassidy says.
"If they have LastPass installed, show the login expired notification and log the user out of LastPass [which] will make it appear to the user that they are truly logged out.
"Once the victim clicks on the fake banner, direct them to an attacker-controlled login page that looks identical to the LastPass one."
Attackers who get into accounts can add themselves as an emergency contact to ensure persistence, he says.
LastPass said email verification will all but neuter the attacks unless email accounts are also compromised.
"The verification process significantly reduces the threat of this phishing attack," the company says in a post to which it is directing concerned social media users.
"The attacker would need to gain access to the user’s email account as well, which could also be mitigated by two-factor authentication for their email account." ®