This article is more than 1 year old
Happy 2016, and here's the year's first ransomware story
JavaScript-ed nasty only spotted on Windows, so far
A security researcher reckons he's spotted the first example of JavaScript-based ransomware-as-a-service, dubbing it Ransom32.
Emsisoft's Fabian Wosar writes here that embedded in a self-extracting WinRAR archive is an NW.js-packaged application that does the heavy lifting for the ransomware.
NW.js, Wosar notes, is a JavaScript framework for application development, based on Node.js and Chromium. It works around JavaScript's normally-strict sandboxing, so a Web application can be repurposed for the desktop without the sandbox getting in the way.
“NW.js allows for much more control and interaction with the underlying operating system, enabling JavaScript to do almost everything 'normal' programming languages like C++ or Delphi can do”, he writes [apparently, someone thought this was a good idea – El Reg].
Because NW.js is a legitimate framework, it's also hard to fit into signature-based malware detection (the company makes the usual observation that unlike everyone else, it can protect users against this attack).
While Wosar's only seen Ransom32 as a Windows attack vector, NW.js would theoretically let the nastyware get packaged up for Mac OS X and Linux systems.
In the copy Emsisoft analysed, once Ransom32 was installed and launched, it connected to a command-and-control server on Tor, negotiated the Bitcoin address victims are supposed to pay to recover their files, and displayed its ransom note:
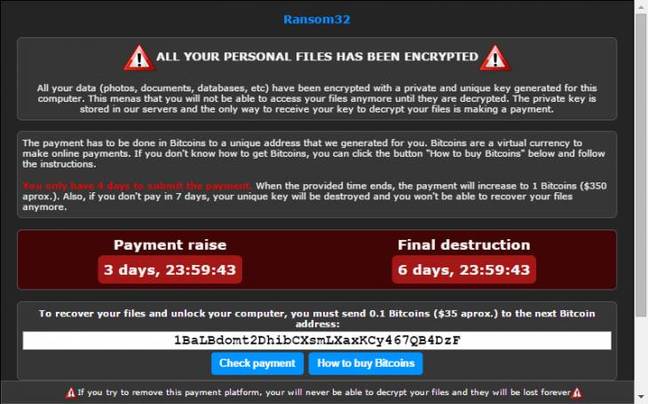
Ransom32's you-are-pwned warning, captured by Emsisoft
The encryption it uses is AES with a 128-bit key. ®
