This article is more than 1 year old
Trustworthy x86 laptops? There is a way, says system-level security ace
ARM isn't the answer either, adds Joanna Rutkowska
32c3 Security concerns around Intel's x86 processors – such as the company's decision to force the secretive Management Engine microcontroller onto its silicon – have raised fundamental questions about trust in personal computers, whatever architectures they may be based upon.
The founder of Invisible Things Labs, security researcher Joanna Rutkowska, delivered one of the first talks to the 32nd Chaos Communications Congress (32c3) in Hamburg on Sunday, restating the issues she considers make Intel x86 "insecure and untrustworthy" before explaining how she believed they may be practically solved in her talk, Towards (reasonably) trustworthy x86 laptops.
The lecture was based on Rutkowska's October paper (PDF), which asserts that most modern operating systems are too trusting, plus her December recommendations (PDF).
That issue is that kernels, drivers, and other low-level code are assumed to be trustworthy even though bugs hidden within them can be exploited to disable whole security mechanisms. Rutkowska added: "A successful exploit against one of the thousands of drivers, networking protocols and stacks, filesystem subsystems, graphics and windowing services, or any other OS-provided services, has been considered unlikely by the systems architects."
Firmware-level vulnerabilities (eg, LightEater) and bungled implementations of boot security (eg, Intel TXT), alongside the small horde of attack vectors introduced through peripherals, provide ample ammunition to attackers, according to Rutkowska.
This means you can't really trust your sensitive data with your hardware, and instead crucial information should really be kept apart from the main machine. She said a "strict separation of state-carrying (trusted) element from the rest of the hardware" has become necessary as people and personal computers become increasingly interdependent.
Rutkowska said the communal effort on improving personal security in the application layer in recent years – from GnuPG and Tor, through to OpenVPN and disk encryption tool LUKS – “is meaningless if we cannot trust our operating system, because the operating system is the trusted part – if it is compromised then everything is lost.”
There have been notable efforts to create a trustworthy operating system stack. Rutkowska herself had started the open-source Qubes OS project five years ago, which now has dozens of contributors. Qubes works by running different applications in their own virtual machines – for example, the VM running a browser used to visit any old website is separate to the VM running GPG; if the browser is compromised, the attacker has to break through the Xen hypervisor to get to the encrypted email client.
Version 1.0 of Qubes OS was released in 2012, while 3.0 was released in October of this year.
The core of her talk dealt with the widespread assumption of trustworthiness in hardware, particular in regards to laptops, which it doesn't deserve.
What's wrong with Intel x86 laptops?
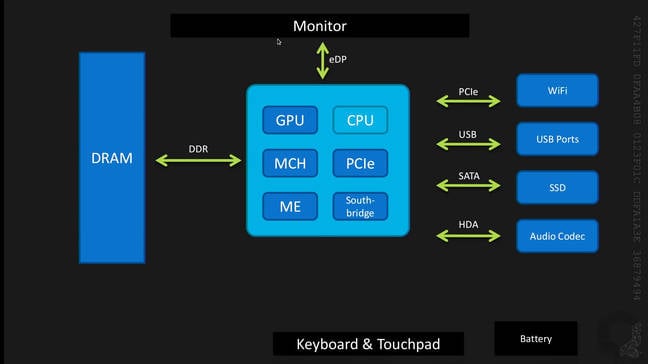
Intel's x86 platform is ubiquitous in modern laptops, and “present Intel processors really integrate everything and the kitchen sink,” said Rutkowska. “Ten years ago we used to have a processor, a Northbridge, a Southbridge, and perhaps even more discrete elements on the motherboard. Today, nearly all of these elements have been integrated into one processor package.
“Of course there is only one company making these,” Rutkowska said. “It's an American company called Intel, and it's a completely opaque construction. We have absolutely no ways to examine what's inside [its chips]. The advantage is that it makes the construction of laptops very easy now, and lots of vendors can produce little sexy laptops.”
Joanna Rutkowska © 2015
When we talk about processors today, we are no longer talking about just the CPU, said Rutkowska. “The processor is now the CPU, GPU, the Memory Controller Hub, PCI express, some southbridge – so for example SATA controller – and so on, as well as something called Management Engine (ME).”
Intel ME is a microcontroller, and part of Intel's AMT hardware and firmware technology which allows administrators to remotely manage the hardware over network – all underneath whatever operating system is running. As this management is conducted at a low-level in the stack, it dodges the OS – meaning overwriting your out-of-the-box Windows installation with a Linux distro will not guarantee any trustworthiness.
The ME microcontroller comes with its own RAM, it can access the system's RAM, and it has its own private ROM of firmware code, which nobody may inspect. “It runs a whole bunch of proprietary programs,” said Rutkowska, “and even runs Intel's own proprietary operating system, and this is all happening whenever you have some power connected to your processor, even in sleep mode, and it could be doing anything it wants.”
She added:
The first thought for security people is that this is an ideal backdooring or rootkitting infrastructure. Which is true. However there is another problem, what I call the 'Zombification' of personal computing.
As a former stealth malware researcher, Rutkowska said she could not imagine a more ideal infrastructure for malware than the Management Engine: “ME has access to everything that is important. It has unconstrained access to DRAM, to the actual CPU, to GPU, it can also talk to your networking card, especially your Ethernet card, the controller for which is also in the Southbridge in the processor. It also has its own dedicated partition on the SPI Flash which can be used to store whatever ME wants to store there. This is really problematic, and we don't know what it runs.”
Zombification
Typically, people run software in the application layer, and expect all the decision making by software to happen there; the low-level code below acts as a middleman, instructing the hardware to do what the users wants it to do.
Citing a book by one of the Intel architects who had designed ME – as “it's about the only somehow official source of information about Intel ME,” according to Rutkowska – the researcher reckons Intel wishes to completely invert this model.
Intel “essentially wants to eliminate all the logic that touches data from apps, and the operating system even, and move it to Intel ME. Remember, Intel ME is also an operating system, a separate operating system... nobody knows how it works. Nobody has any possibility to look at the source code, or even reverse-engineer as we cannot analyse the binaries. It is an operating system which is fully controlled by Intel, as is any functionality it offers,” she said.
The ME blackbox is not trustworthy, says Rutkowska: “The complexity of the architecture … doesn't look like it could be solved effectively.”
Although this seemingly borked Qubes OS's confidence that it could securely lock down and compartmentalize software on a machine, there may be a different way to win the game: “You cannot really win under the old rules," said Rutkowska, who added that it was perhaps time to begin to change those rules. "That starts with recognising that most of the problems here begin with the persistent state.”
