This article is more than 1 year old
Infosec bods rate app languages; find Java 'king', put PHP in bin
Web scripting languages offer XSSive flaws
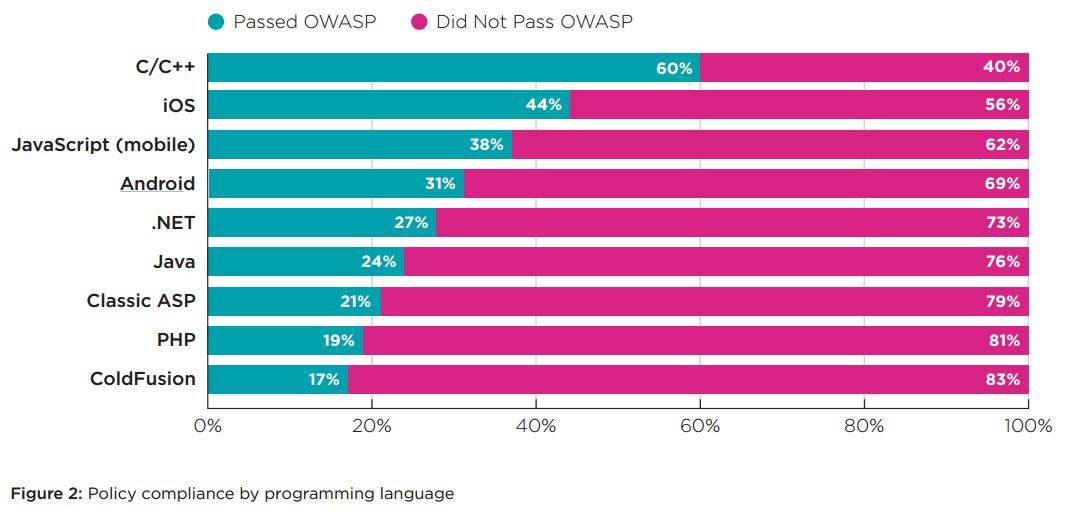
Java applications have been found to have many fewer common vulnerabilities than those coded using web scripting language. Less than a quarter of Java apps sport sporting SQL injection vulnerabilities, compared to more than three quarters of those written in PHP.
So says Veracode's new State of Software Security report (PDF).
The research crawled languages including PHP, Java, JavaScript, Ruby, Microsoft Classic ASP, .NET, C and C++, iOS, Android, and COBOL, scanning 50,000 applications over the last 18 months.
It found PHP apps fared worse than all with 86 percent bearing SQLi, one of the dangerous, perennial, and easy-to-exploit web application vulnerabilities.
More than half of those apps also contain cross-site scripting holes, the other chief web app security irritant.
About two thirds of ASP apps contain SQLi vulnerabilities, with , to no-one's surprise, ColdFusion coming closely behind with 62 percent of applications carrying the bugs.
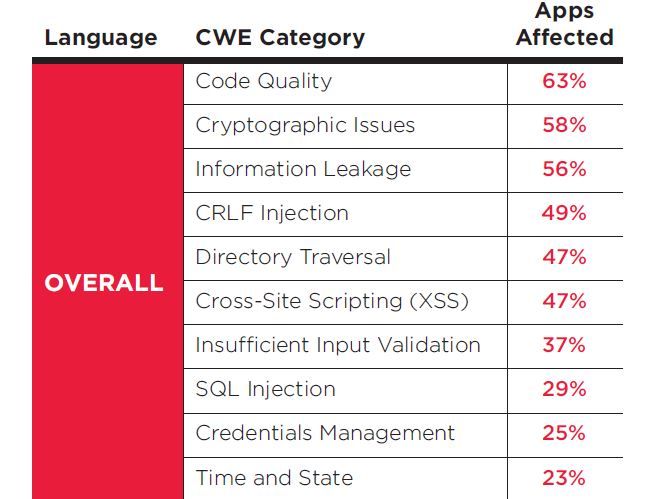
Worse, 80 percent of apps written in PHP, ASP, or ColdFusion flunked kindergarten security tests sporting one of the Open Web Application Security Project's Top Ten quality coding benchmarks.
The Top Ten is held up as the control against which the boilerplate statement "we take security seriously" is measured.
Some 87 percent of Android apps have cryptography implementation issues while 90 percent have code quality issues, more than any other language studied.
“When organisations are starting new development projects and selecting languages and methodologies, the security team has an opportunity to anticipate the types of vulnerabilities that are likely to arise and how best to assess for them,” Veracode security boss Chris Wysopal says.
“The data in this report can inform decisions around language selection, developer training and which assessment techniques to use in order to make the inevitable remediation process less onerous.
"This information can make it easier for security to work with development to increase the maturity of security in the software development lifecycle and produce less risky applications."
Reading an application security book or taking a course will bolster the infosec chops of a developer by about a third, however. ®