This article is more than 1 year old
Comcast resets 200k cleartext passwords, hacker claims breach
Zimbra mail server exploit claimed as source of dump
A hacker has tried to sell 200,000 valid cleartext Comcast credentials he claims he stole in 2013 from the telco's then-vulnerable mailserver.
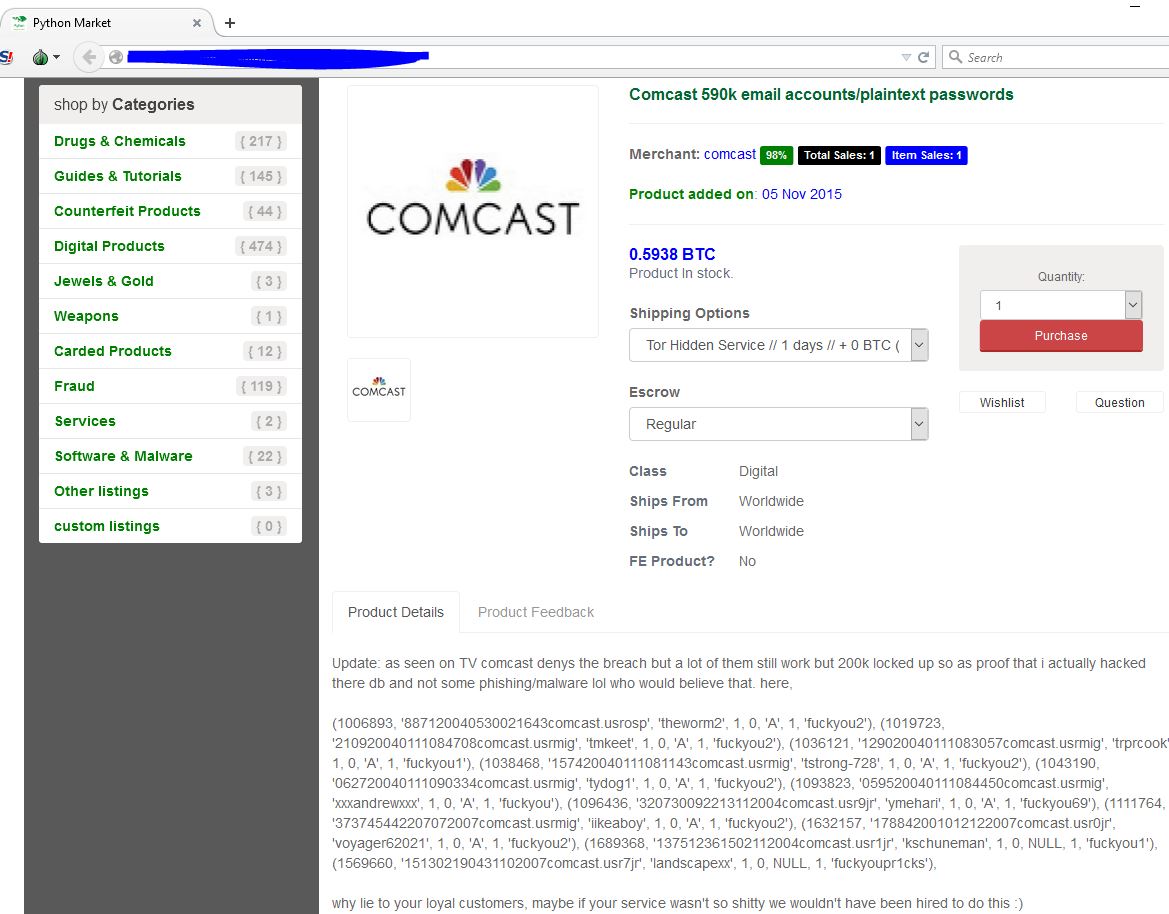
The telco has reset passwords for the affected accounts after news surfaced of the credentials being sold on the Python Market hidden marketplace.
Of the total pool of 590,000 accounts for sale for US$1,000, the company says around a third were accurate.
It told the Chicago Tribune the data was probably obtained through phishing, malware, or a breach of a third party site.
But the hacker responsible for the selling of the credentials, known as Orion, told Vulture South he obtained the credentials when he popped a Comcast mail server in December 2013.
He said the breach yielded 800,000 Comcast credentials of which 590,000 contained cleartext passwords.
Comcast has been contacted for comment.
"So in 2013 December the f****s at NullCrew came across an exploit for Zimbra which Comcast used at this domain *****.comcast.net ," Orion says.
"NullCrew only got [about] 27k emails with no passwords lol while I got 800k with only 590k users with plaintext passwords."
Comcast said it had "no evidence" of the December breach in which the then Zimbra directory traversal vulnerability (CVE-2013-7091) was exploited to gain access to the credentials.
A discussion on Reddit has focused on Comcast's apparent use of cleartext passwords, something regarded as a grand failure in security circles.
Orion claims the pinched passwords were stored as cleartext. ®