This article is more than 1 year old
Five-star Flash phish filched from Hacking Team targets bigwigs
New attack in old gift wrap
The DarkHotel global advanced threat actor group is targeting suit-wearing types with an old-school HTML application stuffed with the Adobe Flash exploit borrowed from stolen Hacking Team data.
The flaws were quickly patched after the Hacking Team goring in July, but DarkHotel appears to have started targeting the exploits before the fixes landed. The group's efforts target the HTML application (.hta) to attack executives in at least nine nations, from Bangladesh, to North Korea and Germany.
Kaspersky researchers say the group will "relentlessly spearphish specific targets" over months in order to pull off a successful compromise.
"The DarkHotel advanced persistent threat group continues to spearphish targets around the world, with a wider geographic reach than its previous botnet buildout and hotel Wi-Fi attacks," the researchers say.
"Some of the targets are diplomatic or have strategic commercial interests.
"[HTA] code results in the execution of internet_explorer_Smart_recovery.exe (a malware downloader)."
The hacking group revealed late last year is known for establishing beachheads in hotel networks from where executives can be targeted over public wifi.
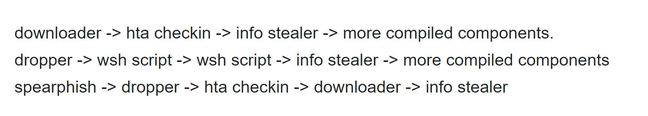
DarkHotel attack chain.
It has added some established phishing tricks to its retinue, including the use of old-school malicious HTA application downloaders first used some 15 years ago in which the Hacking Team Flash vulnerability is contained.
Kaspersky wonks say the group has matured and is more adept at attacking better-defended victims. To that end it is thought to be stockpiling stolen certificates, hiding its malware behind layers of encryption, and is employing counter-analysis techniques to identify anti-virus programs.
Other unnamed Chinese actors have been found using the Hacking Team Flash vulnerabilities in attacks.
One lazy group had simply copied the Hacking Team exploit verbatim and used it within compromised websites including an apparent Chinese Government property according to MalwareBytes researcher Jerome Segura.
"We found a particular attack on a Chinese website where the perpetrators literally copied and pasted the exploit code from HackingTeam, and simply replaced the default calc.exepayload with theirs," Segura says. ®
