This article is more than 1 year old
Australian Cyber Security Centre uses discredited data to quantify infosec threats
The numbers are down, but Australia's Oz Cyber ForceTM says things are getting worse
The cost of “cyber attacks” in Australia appears to be stabilising and the country has never been subject to an attack at the national scale, but the government's Cyber ForceTM (not its real name) is still pitching the growth of the threat.
Along the way, an old and somewhat exaggerated estimate of the cost of cyber incidents has shambled out of the grave, with the Australia Cyber Security Centre telling Australians that hacking is a billion-dollar burden on the economy.
Keen readers of footnotes will observe that the estimate that cybercrime costs us a billion has come not from a government agency, but from the hardly-disinterested Symantec's 2013 Norton report.
As the Australian Cyber Security Centre (ACSC) report notes, “it is difficult to establish an accurate figure for the cost of cybercrime”, and Symantec surely found it so: after its 2011 data point of AU$1.8 billion was challenged, its 2012 report revised the data down to $1.6 billion, and by 2013 it had “grown” to $1.06 billion.
While still growing, the rate of increase of attacks on Australian government networks is also declining.
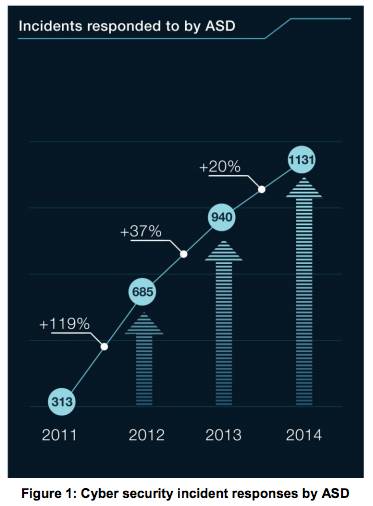
Never mind the trend, feel the growth
The Australian Signals Directorate (ASD), the reporting agency for networks of governments and others “of national importance” reported a 119 per cent growth in incidents between 2011 and 2012, but only a 20 per cent increase in 2013-2014.
Even in absolute terms, the number of ASD-reported incidents flattened out in that period – there were 372 more incidents in 2012 than in 2011, but only 191 more incidents in 2014 compared to 2013.
As The Register has previously reported, the ASD's “protect your network by not being stupid” guidelines was trumpeted as beating all attacks since 2013.
The ACSC generally agrees, but suggests the number of intrusions is non-zero: “the number of confirmed significant compromises of federal Australian Government networks has decreased since 2012”, the report says.
The growth, therefore, must be in the commercial sector, where the report says “In 2014, CERT Australia responded to 11,073 cyber security incidents affecting Australian businesses, 153 of which involved systems of national interest, critical infrastructure and government.”
CERT Australia's breakdown put the energy sector as the favourite target (29 per cent of attacks), followed by banking (20 per cent), the communications industry at 12 per cent, with the IT industry reporting only 4 per cent of the incidents known to CERT Australia.
The ACSC also reckons denial-of-service reports “remained steady” between 2013 and 2014, while malware on the other had is a major problem. “Between 17 October 2014 and 14 January 2015, the AISI [Australian Internet Security Initiative – Ed] reported over 15,000 malware compromises daily to Australian Internet Service Providers (ISPs) for them to action”.
It is, perhaps, unfair for us to criticise all of the ASCS's data sources. It does at least have the good sense to read El Reg, to cite Australia's poor response to Heartbleed. ®
