This article is more than 1 year old
Syrian Electronic Army in news site 'hack' POP-UP MAYHEM
Gigya redirect exploit blamed for pop-rageous ploy
The Syrian Electronic Army has compromised a number of news websites – apparently through DNS redirects via Gigya, a customer identity management platform used by all the sites.
The Pro-Assad javascript popup appeared across several websites, including The Telegraph, The Independent, Forbes, Time Out, PC World and The Evening Standard.
Visitors to the site were shown the following image:
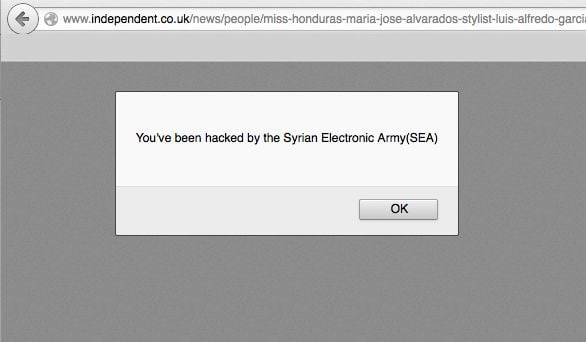
The Telegraph admitted it had been "compromised" and blamed a part of the website operated by a "third party", a party El Reg has since learned is Gigya.
A part of our website run by a third-party was compromised earlier today. We've removed the component. No Telegraph user data was affected.
— The Telegraph (@Telegraph) November 27, 2014
“Some calls to Gigya domains were redirected to the hackers site or showed a hacking message to end users”, Gigya said in a statement.
“It might take some time until the changes propagate to all users. We have worked with GoDaddy to resolve the issue and the redirection was removed.”®
