This article is more than 1 year old
CAPTCHA rapture as 'thousands' affected by seven year-old bug
Fix committed for JQuery validation plugin demo script
A reflected cross site scripting flaw patched overnight may affect millions of websites due to a seven-year-old flaw in a jQuery validation plugin demo script used for CAPTCHA, Dutch penetration tester Sijmen Ruwhof says.
The "severe" vulnerability appeared to have existed in CAPTCHA since 2007 and could lead to session hijacking through reflected cross-site scripting attacks on exposed sites that used the demo script.
Ruwhof stumbled on the then unpatched flaw in jQuery Validation Plugin during an August client penetration test which he claimed had not been patched despite his repeat disclosures over different email addresses linked to jQuery maintainers, all which allegedly fell on deaf ears.
"This security bug seems to have spread to tens of thousands of web sites since its creation," Ruwhof said in a public disclosure.
"It's a wild guess, but I would not be surprised if there are around 20,000 web sites affected by this security bug."
jQuery developer Jorn Zaefferer committed a fix overnight.
"The flaw wasn't in the plugin itself, just in one of the demo files, as the blog post describes as well. Now that the details are available, I've committed a fix," Zaefferer said.
Ruwhof cited instances of researchers reporting flaws that appeared to be ignored by jQuery developers, including one in 2011 by security researcher known as ACC3SS.
"This vulnerability was introduced probably around eight years ago and copied to all kinds of web sites and software products," he said.
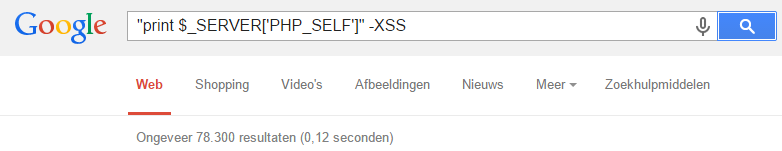
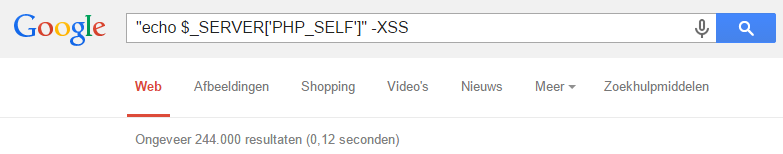
He found that the CAPTCHA demonstration script in line 69 included a PH variable printed without any user input sanitisation, making JavaScript injection possible.
That dodgy code was according to Google searches cited 322,300 times. By perhaps wild extrapolation he said that could mean the code was present in "millions of websites".
The researcher advised site developers to remove the /demo/ folder from the jQuery Validation Plugin which should be non-disruptive for most admins.
"When you've found out that your web site was vulnerable to this attack, then you should perform a forensic analysis to see if someone attacked your web site in the past," he said.
"You can know this by searching for extraordinary requests that are made to the vulnerable file URLs." ®
