This article is more than 1 year old
Eggheads turn Motorola feature phone into CITYWIDE GSM jammer
Innocent mobile turns bad... with good software
Berlin boffins have spotted a procedural flaw in the long-lived GSM protocol and created an exploit around it which can knock out a mobile network or even target an individual subscriber in the same city.
The exploit, presented at the 22nd USENIX Security Symposium last week, takes advantage of the fact that GSM lets phones establish a radio connection before cryptographically authenticating them. That allows a hacked Motorola C123 to masquerade as any handset, before the real device can get connected, denying service to one customer or a whole network.
The 2G telephony standard embodied in GSM has some serious cryptography behind it. Once a radio connection has been established, a key-exchange protocol identifies the customer and encrypts the communication. Before that, however, the handset has to respond to a paging request and it is this response that the boffins have managed to fake.
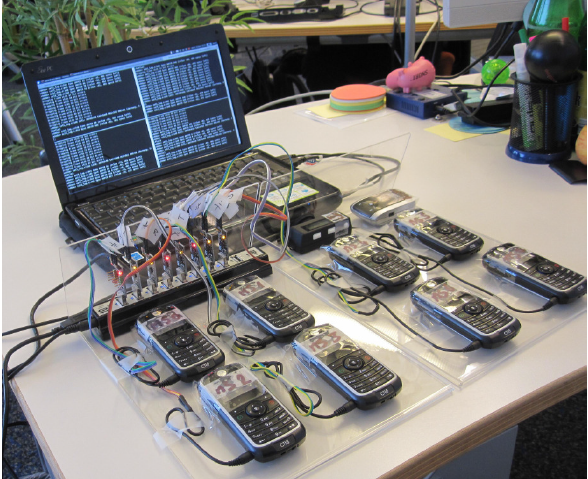
Each phone can block 64 calls or messages a minute
Faking the response won't get you access to the mark's calls or text messages, but it will prevent them arriving at their intended destination. In the presentation paper (PDF, detailed if a little hyperbolic) the researchers argue that the GSM session key could be broken, making it possible to intercept incoming calls, but we'd need to see that in action to believe it was that easy.
But denying service is certainly possible, and the team even managed to deny service to a specific number – which is more concerning, as this would be very hard to detect. Cutting off an individual phone could be very helpful in a number of circumstances.
When a call or text is being routed to a mobile phone the network will only have a vague idea where that phone is. The Home Location Register, which tracks the location of every phone on a network, only knows the Base Station Controller (BSC) to which the phone is attached. A single BSC will be connected to multiple Base Transceiver Stations (BTS), which are the base stations with which we're familiar.
So a paging request will be sent out to every BTS connected to the known BSC, which might cover a significant area. The hacked phone simply responds to every paging request and is allocated a radio slot, before failing the authentication stage. In turn this causes the call to fail, with the intended recipient never being alerted.
Responding to every paging request isn't easy. The team demonstrated that their software can outperform any normal handset (responding before the legitimate recipient can get a word in) but when the hacked phone is occupying the allocated channel it can't listen for more paging requests, so the team calculate that one handset can block a maximum of 64 requests a minute. The Berlin network tested by the team was paging between 400 and 800 handsets every minute (depending on the popularity of the network) so blocking an entire operator from large geographical areas is clearly possible.
Locking out a specific phone is a little harder as the paging requests are addressed using the Temporary Mobile Subscriber Identity (TMSI), a random number agreed between the handset and the network to avoid any real identities being transmitted.
To find a specific TMSI the team made repeated calls to the target's phone number, while listening for paging requests. By recording all the TMSIs paged, and hanging up the call before the recipient's phone rang, they were able to establish the TMSI of a specific phone within 20 calls.
Once they'd done that it was trivial to set their hacked C123, connected to a PC for faster processing to respond to every paging request addressed to that TMSI, which then denied service to that customer.
The team points out that on networks where no encryption is used (such as in Pakistan and other countries on the US ITAR list) it would also be possible to hijack the call without the caller ever knowing it had happened. They also propose that the session key could be intercepted and cracked during an earlier call, claiming that if it hadn't been refreshed in the interval between interception and decryption then actual interception would be possible.
El Reg adds that the encryption level is specified by the network and GSM authentication isn't mutual, so this technique could be combined with a faked base station (which would specify no encryption) to allow a true man-in-the-middle attack.
3G networks do mutually authenticate, though they also establish a radio connection prior to authentication so could be vulnerable to a similar attack – likewise with 4G networks.
Fixing the problem would mean changing the GSM protocol, which isn't very likely. Operators could also keep track of radio links which failed at the authentication stage, which would enable them to alert a user if it was happening – though not by call or text, obviously.
Targeted attacks are much more likely than citywide jamming. Attractive as the idea might be, it would require considerable resources (to research the network and position the hacked equipment) and the effect would be swiftly mitigated as the network became aware of what was happening - but block a single user and likely no-one would ever know about it, making it probable that someone, somewhere, is already doing just that. ®
