This article is more than 1 year old
Cisco revs up Nexus switches to 40GE with fresh ASICs
Other tweaks, SDN promises, and a VPN tunnel for control freaking public clouds
Other stuff gets some tweaks
Cisco also made a bunch of related announcements on Monday in the Nexus product line.
First, there will be a 40GE expansion module for the Nexus 5500 switches, which is expected to be available sometime in the first half of this year. Pricing will be available when it comes out.
Cisco also announced a new Nexus 2248PQ 10GE switch with 40GE uplinks, which is available now and costs $12,000. The feeds and speeds of this box were not available at press time.
As promised, Cisco is launching its first "services blade" for the Nexus 7000 core and aggregation switch. This particular one is the network analysis module, or NAM, and as the name suggests it will bring application awareness and performance analysis for Layers 4 through 7 in the network stack to the Nexus 7000 switches.
The NAM will be available as a plug-in card called the NAM-NX1 sometime in the first half of this year, and will also be available in a format compatible with VMware's ESXi hypervisor and deployed in a virtual machine as the vNAM. Pricing for the hard and soft versions of the NAM will not be given out until it ships. vNAM will enter customer trials in the second quarter.
Another new feature is called Nexus 1000V InterCloud – but before you jump to conclusions (like I did), this is not a funky version of the Nexus 1000V virtual switch created by Cisco that runs out on public clouds and is somehow magically synchronized with Nexus 1000V virtual switches running in your data center. Such a thing might be useful, in theory, but the Nexus 1000V is not the preferred virtual switch out there on the public clouds.
Open vSwitch and the embedded switches inside of ESXi and Hyper-V are popular, when virty switches are required, and heaven only knows what Amazon is using in conjunction with its homegrown variant of the Xen hypervisor that underpins its EC2 compute cloud.
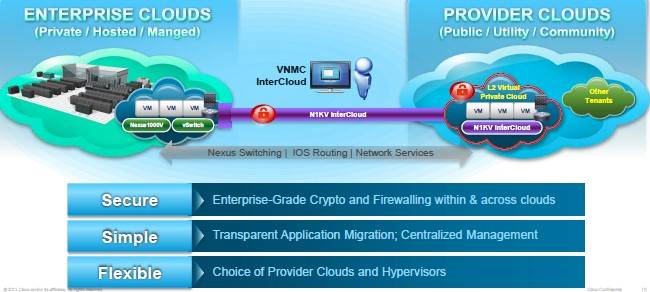
The Nexus 1000V InterCloud tunnel out to private clouds
What the Nexus 1000V InterCloud program is, however, is a hypervisor-agnostic virtual private networking tunnel that works with Cisco's physical Nexus switches and its Nexus 1000V and other virtual switches running with hypervisors on servers to link out to Layer 2 virtual private networks running on clouds to bring them into the same management domain as the internal cloudy networks.
This InterCloud tunnel has what Huitema called enterprise-grade cryptography and firewalling within the cloud and over the pipe out to the cloud from your data center. So all of the VLANs and policies that your network admins have set up for internal networks can now be extended out to the networks on the public cloud.
A tool called the Virtual Network Management Center, or VNMC, gives that single pane of management to the internal and external networks. You use Cisco's Virtual Security Gateway to encrypt it and Cisco's Adaptive Security Appliance to give it firewall services.
The InterCloud VPN tunnel and VNMC software will be available – wait for it – sometime in the first half of 2013, and pricing will be announced at availability.
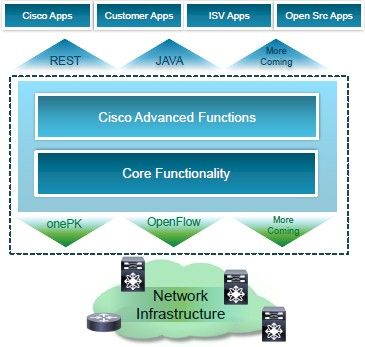
Block diagram of the Cisco ONE software-defined networking strategy
On the software-defined networking front, Cisco is cooking up a strategy and a set of products that it introduced back in June 2012 called the Open Network Environment, or ONE. It provided some milestones for the ONE effort along with the new Nexus 6000 switches.
The ONE architecture includes supporting OpenFlow and other unnamed SDN standards in the control and forwarding planes of switches and routers, but it is more than that. It also includes management and orchestration services, network services above OpenFlow and transport services below OpenFlow, all available through a common set of APIs that will be exposed in all switches and routers running in Cisco's IOS, IOS-XR, and NX-OS operating systems.
The ONE development kit, called onePK (with the capitalization all messed up on purpose by Cisco), will expose these APIs to both network admins and network application developers.
Here's how the ONE effort is coming along. The ONE Controller, which will implement OpenFlow controller protocols, and the Nexus 3000 switches with OpenFlow support, will be available – again, wait for it – during the first half of 2013. Catalyst 3000 and 6500 switches, Nexus 7000 switches, and ASR 9000 routers are in customer trials or soon will be during the first half of this year. The openPK development tools are being tested on ISR G2 and ASR 1000 routers and Nexus 3000 switches now, and will be available in the first half, and will be entering testing on ASR 9000 routers and Nexus 7000 switches also in the first half.
In addition, Cisco is working on support for the Nexus 1000V virtual switch for the Hyper-V hypervisor from Microsoft during the first half of this year, and says that support for the KVM hypervisor from Red Hat is in proof-of-concept with no publicly available timeline for commercial delivery. Support the VXLAN gateway method of uniting public and private clouds, or multiple distinct data centers, is also due in the first half for the Nexus 1000V virtual switch. ®
