This article is more than 1 year old
VeriSign SSL certs open to tampering, competitor warns
Bank of America attacks made easy
VeriSign and one of its partners have come under fire for publicly exposing webpages used to process customer security certificates, a practice a competitor claims puts some of the biggest names on the web at risk of serious targeted attacks.
According to Melih Abdulhayoglu, CEO of internet security firm Comodo, publicly accessible pages such as those here and here needlessly disclose sensitive internal information about VeriSign customers Bank of America and the Commonwealth of Massachusetts respectively. By exposing the email address of the organizations' security certificate managers and providing a comprehensive list of web addresses that use secure sockets layer protection, VeriSign puts them at risk of targeted phishing attacks, he said.
What's more, Abdulhayoglu pointed to the availability of this page provided by VeriSign partner Getronics.nl of the Netherlands. It allows anyone in the world to search its database and pull up a wealth of information about the digital certificates of not only Bank of America but plenty of other companies, including VeriSign itself. The interface also points to dynamically generated pages like the one captured below, which provide buttons for revoking, renewing, and replacing the digital certificate.
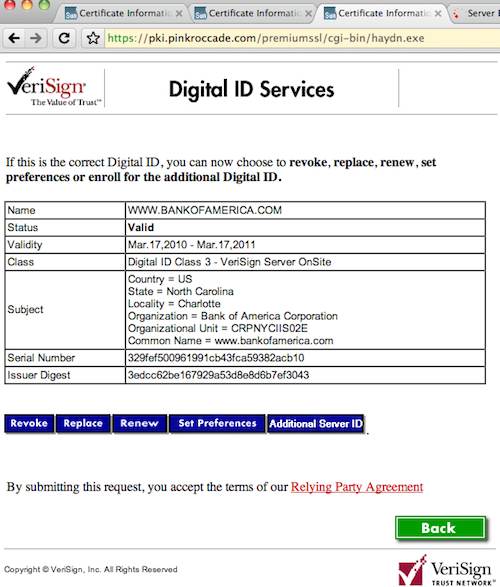
A management page for Bank of America, courtesy of PinkRoccade.com
When The Register looked at the pages from Getronics.nl on Wednesday evening, they continued to prompt users who wanted to revoke a certificate for a challenge phrase. By Thursday morning, users got an error message. The cause of the errors was not known.
Abdulhayoglu said members of his team alerted VeriSign to the easily accessible pages privately, and the latter company insisted they posed no risk to its customers. Comodo then went public with what it called a “serious security vulnerability.” VeriSign responded with its own posting laying out why managers there strongly believe Comodo's advisory is unfounded.
In the balance is the control of the digital certificates that banks, e-commerce sites and other online businesses use to encrypt credit card numbers in transit and prove to customers their servers are genuine. While by no means perfect, the SSL, or secure sockets layer, protocol is one of the most important and widely used systems for protecting end users conducting sensitive transactions online. The ability of outsiders to tamper with them could be devastating.
“There are no winners in this,” Abdulhayoglu told The Register in explaining why he blew the whistle. “Comodo loses, VeriSign loses, their customers lose. We gave them ample time, but if they kept denying it was a vulnerability we had no choice but to go public.”
Tim Callan, VeriSign's vice president of product marketing, has responded that Comodo's warning is based on a fundamental misunderstanding of the publicly exposed pages. He said they aren't administrative panels that give end users the ability to make sensitive changes to certificates. Rather they are “request pages” that employees inside an organization use to ask an authorized certificate administrator to make changes.
“I understand where an outsider might look at this and think that they're looking at something where they can really do powerful things to certificates, but at the end of the day, those powerful things are done by somebody else,” he said. “That control is only accessible by somebody who has a special what we call administrator certificate that is actually on the computer from which they're accessing it.”
It was unclear if Callan's explanation referred to pages on both domains, or only to those on verisign.com. In a later email, he described a page on pinkroccade.com as a "certificate management page." Attempts to get a clarification weren't successful.
The Register was unable to test whether the pages give unauthorized parties the ability to make changes, because it would almost certainly be a felony to do so. But Abdulhayoglu said he is confident they do, at least in certain cases. He acknowledged that the pages require people revoking pages to enter a “challenge response,” but he said those credentials are often contained in what are called CSRs or certificate signing requests that in many cases can easily be found online.
Marsh Ray, a software developer at two-factor authentication service PhoneFactor, was also unwilling to test whether Comodo's report is correct, but he said the advisory sounded plausible.
“This appears to be all that you need to revoke the cert, given that you already get to the customer's management page on the website,” he said.
Callan said CSRs have long included fields designated “Challenge” but that they are disregarded by VeriSign, and customers can leave them blank or input them with any text of their choosing. VeriSign has never instructed customers to put their revocation challenge phrase in their CSRs, the VeriSign VP added, although he wasn't aware of any guidance explicitly telling customers that the passwords should never be included there.
In the event a customer has included the password in one of their CSRs, VeriSign will replace the certificate for free, he added.
In the end, The Register was unable to verify Comodo's claims that the publicly accessible pages allow unauthorized parties to make changes to VeriSign customers' authentication certificates. But it seems a fair point that they needlessly expose information that would better be kept private.
VeriSign would probably argue that they serve a crucial function by streamlining the process of requesting and allocating large numbers of the electronic documents inside big organizations. But sometimes security should trump convenience, and this very well may be the case here. ®
