Original URL: https://www.theregister.com/2014/03/12/snowden_docs_show_nsas_malware_turbine_can_pump_out_millions_of_malware_attacks/
NSA's TURBINE robot can pump 'malware into MILLIONS of PCs'
Sysadmins, routers, criminals' IRC botnets, and maybe terrorists, all for the pwning
Posted in Security, 12th March 2014 21:47 GMT
Updated The latest batch of top-secret intelligence documents from the hoard collected by NSA whistleblower Edward Snowden detail the massive increase in the agency's use of its Tailored Access Operations (TAO) hacking unit – including a system dubbed TURBINE that can spam out millions of pieces of sophisticated malware at a time.
The presentation slides, published by The Intercept, show that 10 years ago the NSA had infiltrated and tapped a modest number of computers, but has since hugely bolstered its toolkit and increased its target list. Within eight years, the number of active pieces of implanted spyware was in the tens of thousands, and slides show an extensive arms catalog of malware for the TAO team to choose from.
"One of the greatest challenges for active SIGINT/attack is scale," explained one presentation from 2009, marked top secret. "Human 'drivers' limit ability for large-scale exploitation (humans tend to operate within their own environment, not taking into account the bigger picture)."
The solution was to build TURBINE, which can carry out "automated implants by groups instead of individually," and scale to operate millions of implants at a time. This command-and-control server includes an "expert system" that automatically picks the right malware for a victim and installs it on their computer, thus "relieve the [TURBINE] user from needing to know/care about the details."
TURBINE was active from at least July 2010, the documents state, and has infected up to 100,000 devices and machines, with more planned. According to the agency's 2013 budget files, some of the $67.6m of taxpayer dollars allocated to the NSA's TAO team went to maintaining and developing the system.
TURMOIL hunts the sysadmin
TURBINE also links into a NSA sensor system dubbed TURMOIL, which taps into computer networks around the world to monitor data traffic and identify potential targets. It can track down a mark from their email address or IP address, which device he or she is using, or by web cookies from Google, Microsoft, Twitter, Yahoo! and others.
While terrorist targets are mentioned, it's clear from the documents that system administrators are also high on the todo list for the TAO team. One comment on an internal NSA message board system was titled simply: "I hunt sys admins."
"Sys admins are a means to an end," it states. "Once you have control of the IT manager's computer then it's easy to monitor any "government official that happens to be using the network some admin takes care of."
Pwning the sysadmin is useful for malware attacks against large commercial routers and to defeat VPNs. The documents detail two pieces of NSA-developed malware, HAMMERCHANT and HAMMERSTEIN, which are designed to sit on routers and eavesdrop on VoIP traffic, and grab encryption keys to decrypt supposedly secure VPN connections, all in real time.
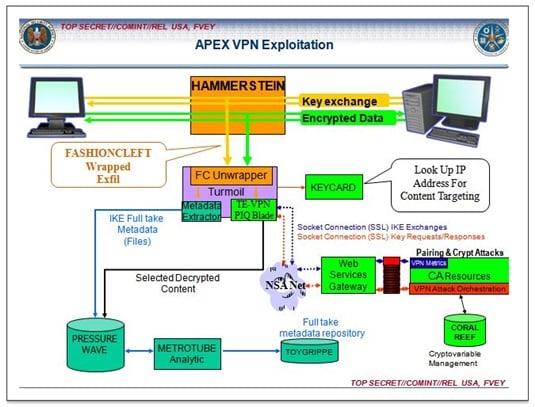
Taking the private out of VPN
Other malware includes code called QUANTUMSKY, developed in 2004, which can block access to websites, and a 2008 creation dubbed QUANTUMCOPPER which automatically corrupts any data downloaded by a user.
TURBINE is run though stations at the NSA's headquarters in Maryland, along with ancillary offices in the British Menwith Hill facility and from Misawa, Japan. Documents show the UK's GCHQ has been active in developing exploits for TURBINE and that it uses information gleans from the system, as do the other "Five Eyes" nations of Canada, Australia, and New Zealand.
"All of GCHQ's work is carried out in accordance with a strict legal and policy framework which ensures that our activities are authorized, necessary and proportionate, and that there is rigorous oversight," the British intelligence agency said in a statement.
Inside Uncle Sam's malware war chest
The Snowden documents show that the TAO team now has access to a very sophisticated toolkit for implanting trackers on systems, and how the methods of spreading the code have evolved to match consumer behavior.
A 2012 presentation complains that the traditional method of infection, spamming out infected attachments, was only achieving a one per cent success rate because people are getting smarter about avoiding potentially malicious downloads. To get around this, the agency switched to browser attacks, which it said upped success rates to 80 per cent in some cases.
Targets visiting certain websites were redirected to an NSA WILLOWVIXEN server, allowing software called FOXACID to find a browser vulnerability and exploit this to compromise the PC or handheld. The documents claim that a fake Facebook server was set up for this purpose and used to distribute malware dubbed QUANTUMHAND, which went live in October 2010.
"If we can get the target to visit us in some sort of web browser, we can probably own them," a TAO team member reports in one document. "The only limitation is the 'how.'"
Other code, called SECONDDATE uses a man-in-the-middle attack to allow "mass exploitation potential for clients passing through network choke points, but is configurable to allow surgical target selection as well."
A 2010 presentation also gives details about the QUANTUM family of malware developed by the government for attacking systems. This includes code for the redirection of web traffic, controlling crooks' IRC botnets, hijacking DNS, and corrupting downloads.
Another malware system, called UNITEDRAKE, comes with a selection of plugins for different purposes, each with its own classification. The CAPTIVATEDAUDIENCE plugin will take over a system's microphone to record conversations, FOGGYBOTTOM will record internet history and login details, and SALVAGERABBIT copies the contents of any flash drives plugged into the machine.
The agency is well aware that antivirus companies are on the lookout for new and interesting malware samples, particularly after the Flame debacle. A NSA trojan dubbed VALIDATOR can be set with an automatic self-destruct sequence and delete itself from a target's system after a set period.
The madness is spreading
Despite efforts to limit the exposure of its systems to outside interest, the documents show that the NSA is aware that other governments are copying their techniques.
"Hacking routers has been good business for us and our 5-eyes partners for some time," notes one NSA analyst in a top-secret document dated December 2012. "But it is becoming more apparent that other nation states are honing their skillz [sic] and joining the scene."
This is already worrying security analysts, and was top of the agenda at last month's TrustyCon conference. F-Secure's malware research chief Mikko Hyppönen told the summit that so far government-developed malware was coming from Germany, Russia, China, and even Sweden, and there was a thriving trade by ethically challenged companies willing to develop malware for repressive regimes.
Similar concerns were echoed at the RSA 2014 conference, with the company's chairman Art Coviello calling for an international moratorium on attack code before the situation gets out of control. If government cyberattacks are normalized then the effects on the general public could be catastrophic, he noted, but there's no sign of a change of policy from the NSA.
"As the [US] President made clear on 17 January," the agency said in a statement, "signals intelligence shall be collected exclusively where there is a foreign intelligence or counterintelligence purpose to support national and departmental missions, and not for any other purposes." ®
Updated to add
You may be interested to know that the NSA has responded to the claims first published by The Intercept.