Original URL: https://www.theregister.com/2013/10/10/vbulletin_vuln_opens_backdoor_to_rogue_accounts/
vBulletin vuln opens backdoor to rogue accounts
The workaround is easy, though
Posted in Security, 10th October 2013 01:05 GMT
The widespread vBulletin CMS has a vulnerability that allows remote attackers to create new administrative accounts.
Back in August, users of versions in the 4.1+ and 5+ series were advised to delete the /install/ or /core/install/ directories (depending on version) as a workaround against the bug, but vBulletin didn't advise of the impact of the problem.
However, according to this article at Help Net Security, the vulnerability allows admin account injection using vulnerable PHP code.
A user whose site was compromised in September posted an Apache log that identified the attack source (below).
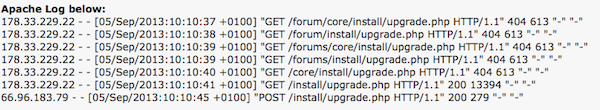
The vulnerable upgrade.php resource is attacked to inject the unwanted administrative user account.
The author of the article, Barry Shteiman of Imperva, notes that the exploit code and technique were found on hacker forums, meaning that the exploit is in the wild.
If the vBulletin user can't, for some reason, delete the /install/ or /core/install/ directories, Shteiman advises that they implement redirects to block incoming requests trying to hit the upgrade.php file. ®