This article is more than 1 year old
Extortionist hacks IT provider used by the stars of tech and big biz, leaks customer info after ransom goes unpaid
'Many companies pay us for our work, and we do not publish data and help them to eliminate vulnerabilities'
A service provider hired by the likes of Oracle, SAP, BT, and many others, to manage their IT systems has been hacked – and its client data held to ransom.
At the turn of this month, Germany-based CityComp was broken into by a miscreant, who pinched troves of private information from its customer database and threatened to publicly reveal all that stolen data unless a ransom was coughed up.
The hacker, going by the name Boris, told The Register that right now a partial sample of the swiped info is available to download from a Tor-hidden dark web site, and because the ransom was not paid by CityComp, the full archives are set to be released today. Boris claimed the price was $5,000, though CityComp disputes this and says it was more than that.
CityComp boasts it looks after "more than 70,000 servers and storage systems of all types and sizes in up to 75 countries. In addition, we provide support for more than 500,000 client hardware (PC, workstation, printer, cash register)."
In other words, it's hired to install, maintain, repair, and remove IT equipment for scores of companies, ranging from Oracle, SAP, BT, Toshiba, VW and Airbus to Porsche, Hugo Boss, Ericsson and ATOS.
According to Register sources who have seen the partially leaked information, the data so far includes things like contact information for CityComp's customers – such as names, email addresses and phone numbers – notes of meetings with clients, and IT equipment inventories, such as model numbers, specifications, and serial numbers. How much is available to download depends on the victim: some have a few spreadsheets of contact details leaked, and some have what's said to be long lists of installed computer gear and other documentation.
This information could be useful to criminals seeking any inside information to pull off targeted cyber-attacks against certain corporations. We're not talking direct identity theft, here.
According to Boris, "312,570 files in 51,025 folders, over 516 Gb data financial and private information on all clients, include VAG, Ericsson, Leica, MAN, Toshiba, UniCredit, British Telecom and etc," was stolen from the German service provider.
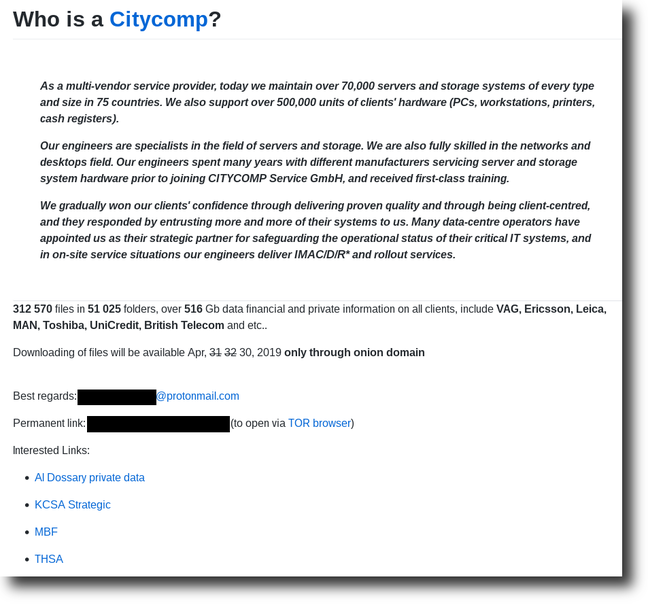
Swag ... Screenshot of dark-web site offering some of the stolen materials for download, redacted for privacy reasons (Credit: Register sources)
Michael Bartsch, of infosec outfit Deutor, which was drafted in to handle the aftermath of CityComp's network intrusion, told El Reg "the stolen data is mostly data about hardware inventories, like hardware type, OS, memory, serial numbers, etc. Only a few personal data records were affected."
Bartsch, who was authorized to speak on behalf of CityComp, also confirmed that while the cyber-break-in was eventually thwarted, affected servers unplugged, and security shored up, more customer information may well leak out beyond what's already available because CityComp "does not yield to blackmail." German cops and prosecutors have also been alerted, according to Bartsch, who told us:
CityComp Service GmbH was the victim of a targeted cyberattack in early April 2019. A still unknown perpetrator has stolen customer data of CityComp and threatened the company with publication, should it not comply with the blackmail attempt.
CityComp with the help and support of external experts and the State Criminal Police Office of Baden-Württemberg successfully fended off the attack and implemented supplementary security measures of all systems. The incident analysis of Deutor Cyber Security Solutions GmbH, G DATA Advanced Analytics GmbH and the Federal State Police Baden-Württemberg showed that at no point any indication for a risk of further infection of customer and partner systems, but for security reasons some of the systems have nevertheless been disconnected.
Since CityComp does not comply with blackmail the publication of customer data could not be prevented. The stolen data has now been published by the perpetrators and CityComp's customers were informed about it.
In cooperation with the State Office for Criminal Investigation Baden-Württemberg suitable measures for prosecution were initiated. At an early stage CityComp was transparent and informed the relevant data protection authorities and customers about the cyberattack and data theft. Full transparency was in place right from the start.
Due to this cyber-attack CityComp has implemented further technical and organizational measures to increase its security in order that such an attack will not occur again in the future.
Finally, Boris told us that CityComp at first showed interest in paying the ransom in exchange for his or her silence and technical details of the intrusion, but it appears once the service provider learned of the vulnerability exploited by the hacker to steal the information, it backed out, fixed up the hole, and refused to pay. Boris claimed many companies cough up the cash to keep leaks private and holes patched when he or she contacts them.
"At the beginning of our communication, they [CityComp] agreed that they will pay for our work and we will help them to eliminate vulnerabilities in their network, but they deceived us," said Boris. "Many companies pay us for our work, and we do not publish data and help them to eliminate vulnerabilities."
We've contacted many of CityComp's customers affected by this security breach, first reported earlier today by Motherboard, including Oracle, BT, Airbus, Ericsson, Hugo Boss, NH Hotels, and Toshiba. Spokespeople were not available for immediate comment. ®
Additional reporting by Iain Thomson.
