This article is more than 1 year old
RedDrop nasty infects Androids via adult links, records sound, and fires off premium-rate texts
Baidu users, beware
A newly discovered strain of Android malware makes live recordings of ambient audio around an infected device.
The RedDrop nasty also harvests and uploads files, photos, contacts, application data, config files and Wi-Fi information from infected kit. Both Dropbox and Google Drive are being used as temporary storage by the attackers.
Infected devices submit expensive SMS messages to a premium service, enriching crooks in the process. Hundreds of infections related to the malware have been spotted by security firms, with Chinese users among the most heavily affected.
Enterprise mobile security firm Wandera discovered the malware when an employee from a US-based "Big Four" consulting firm used their mobile web browser to click on a link displayed on Chinese search engine Baidu. The user was then directed to a site displaying adult content, which was detected as suspicious and blocked.
Upon further investigation, Wandera discovered 53+ innocent-looking apps that front-end the malware, as well as an intricate distribution network of 3,000+ hosting locations, used to maximise reach to end-user devices. "We believe that the multiple distribution URLs, the distinct web properties used to host the APKs and the countless versions of each bit of added functionality all point to the attacker’s attempt to keep the malware from becoming stale and subject to signature-based blocks," Wandera said.
Apps ranging from business tools to games have been contaminated to carry the malware, according to Wandera. Chinese search giant Baidu.com and the Sky Mobi Android app store are both being abused to distribute the nasty.
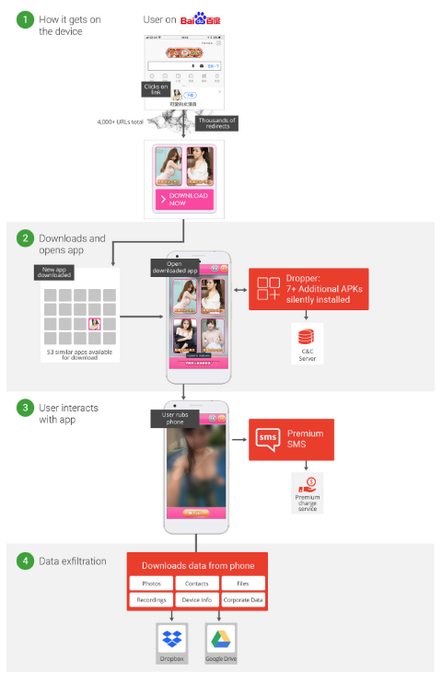
RedDrop Android malware infection cycle [Source: Wandera]
The threat is one of the most advanced examples of Android malware Wandera has seen. "From the download sites and referrers to the C&C and data exfiltration, the attackers who built this malware planned it well," the firm concludes. "On the device itself, the malware was designed to be resilient and to persist across system changes and updates."
Security watchers at Kaspersky Lab are less impressed by the threat, which they reckon has largely been a problem for Chinese smartphone users searching for smut.
"Kaspersky Lab is aware of this threat since September 2017," said security research staffer Victor Chebyshev. "RedDrop is malware capable of spying on its victims (it can collect data about a victim's device, including data from memory card and contacts list) and discreetly make a device buy paid-for subscriptions, which can result in users facing financial risk.
"We have seen hundreds of unique RedDrop detections across the world, mostly from Chinese users. The malware is spreading via third-party platforms that disguise the software as adult applications. Kaspersky Lab products have successfully detected and blocked RedDrop from September 2017." ®
