This article is more than 1 year old
Shock horror! Telegram messaging app proves insecure yet again!
Unicode clumsiness allowed months of malware installations
Telegram has fixed a security flaw in its desktop app that hackers spent several months exploiting to install remote-control malware and cryptocurrency miners on vulnerable Windows PCs.
The programming cockup was spotted by researchers at Kaspersky in October. It is believed miscreants have been leveraging the bug since at least March. The vulnerability stems from how its online chat app handles Unicode characters for languages that are read right-to-left, such as Hebrew and Arabic.
A JavaScript file could be sent as a message attachment to a victim, with the filename crafted to exploit the Unicode bug and cover up the fact it's a .js document. This tricks the mark into opening what appears to be a safe .png attachment. Windows asks the victim if they are sure they want to open the JavaScript file: if they select "Run," or configure their PC to not bother asking, then the script is executed, and malware is downloaded and run.
This software nasty can open a backdoor, snoop on the mark, mine alt-coins, and so on. Telegram has, we're told, corrected the mistake in its open-source application.
"The special nonprinting right-to-left override (RLO) character is used to reverse the order of the characters that come after that character in the string," Kaspersky's Alexey Firsh explained today.
"In the Unicode character table, it is represented as ‘U+202E’; one area of legitimate use is when typing Arabic text.
"In an attack, this character can be used to mislead the victim. It is usually used when displaying the name and extension of an executable file: a piece of software vulnerable to this sort of attack will display the filename incompletely or in reverse."
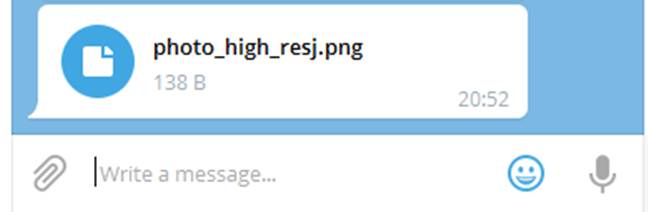
Insecurity via obfuscation ... A .JS file disguised as a .PNG using Telegram's Unicode handling bug
The Kaspersky crew discovered hackers exploiting this blunder in a number of ways. First off it was being used to trick victims into installing a remote-access trojan that would regularly ping Russian servers, and opened a backdoor so that miscreants to remotely control the infected system.
In keeping with current trends, hackers were also using the security hole to install multiple copies of cyber-cash mining software that crafted Zcash, Fantomcoin and Monero coins.
"It appears that only Russian cybercriminals were aware of this vulnerability, with all the exploitation cases that we detected occurring in Russia. Also, while conducting a detailed research of these attacks we discovered a lot of artifacts that pointed to involvement by Russian cybercriminals," Firsh's advisory read.
"We don’t have exact information about how long and which versions of the Telegram products were affected by the vulnerability. What we do know is that its exploitation in Windows clients began in March 2017. We informed the Telegram developers of the problem, and the vulnerability no longer occurs in Telegram’s products."
It has been less than a year since the last big Telegram flaw, and there have been persistent questions about its security. The fact it doesn't encrypt messages end-to-end by default, and that it uses its own homegrown cryptography, worries experts. Telegram insists its software is secure.
Activists in repressive regimes may want to use something more tried-and-tested, such as Signal, to avoid accidentally beating themselves to death while committing suicide. ®
