This article is more than 1 year old
Amazon explained ‘Key’ crack before it shipped fix, says hacker who found the hole
BezosMart doesn’t like being told it was w…wr…wrong
The researcher behind the teaser of a new method to crack Amazon.com’s “Key” connected door locks has revealed how his method works, and criticised Amazon’s response to his work because it detailed the flaw before shipping a fix.
In a Medium Post, the researcher known as “MG” explained that he revealed his riff on an attack vector identified by Rhino Security Labs and publicised his activities.
“A professional researcher saw this and reached out to me, offering to broker a disclosure with Amazon,” MG explained. “Unfortunately, this attempt failed. Amazon turned down the offer by demanding a working PoC be made for them.” MG was also told that Amazon has no bug bounties “or other reward pathways.”
“I wasn’t interested in a reward, but this level of arrogance was off-putting,” he wrote. “So I made the PoC”.
The Register and others reported his handiwork and - surprise! – Amazon suddenly wanted to talk and MG “started helping them understand the attack.”
“I was impressed with the security response team,” he said, but found that when they asked for his code it “was a bit frustrating in context of the initial ‘lol we won’t give you anything but do work for us’ interaction”.
Amazon’s security team then went quiet. But the company’s PR team started saying MG’s hack was nothing to worry about and then explained it in full to Forbes – but before a fix had been implemented (and without even acknowledging The Register’s inquiries about MG’s initial post).
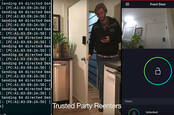
With Amazon revealing details in public, MG decided there was no reason not to disclose his method, which involves scanning the rate of frames produced by Key’s companion camera. That rate spikes when a delivery is made, because the camera records it.
Next, MG employed a Wi-Fi “de-auth” attack – a kind of DDOS – on the camera and lock with his Raspberry-Pi-powered Wi-Fi snooper.
“If the timing is right, you prevent a response from the lock informing the consumer app from knowing that the lock event was successful. For whatever reason, the app was not created to handle this error condition. The UI is also non-responsive, which opens up the opportunity for an inattentive app user to believe they actually pressed the button requesting a re-lock.”
To make the attack more convincing, the RPi plays audio of the Key locking.
MG’s post ends with a host of questions for Amazon about different ways to fool homeowners, delivery staff, or both, that would make this crack or others easier to pull off, and expressed his hope that Amazon takes the ideas seriously because its response to his ideas suggests it’s not thinking too hard about how the Key can unlock criminal possibilities. ®