This article is more than 1 year old
Scammers become the scammed: Ransomware payments diverted with Tor proxy trickery
Of course this does nothing for victims' encrypted files
Cybercriminals are using Tor proxies to divert ransomware payments to their own Bitcoin wallets.
Ransomware scammers have long directed victims to payment portals on the Tor network. For those who do not want to or cannot install the Tor browser necessary to pay their ransoms, operators generally direct victims to a Tor proxy such as onion.top or onion.to, which allows users to access the Tor network via standard web browsers.
But, in what appears to be the first such attack of its kind, operators of a onion.top proxy are performing man-in-the-middle attacks to substitute their own Bitcoin payment addresses for those originally specified in selected ransomware strains, net security firm Proofpoint reports.
Proofpoint learned of the tactic through a message on the LockeR ransomware payment portal urging victims not to use onion.top to pay their ransoms. Payments destined for crooks behind the GlobeImposter and the Sigma ransomware have been targeted in the same scam.
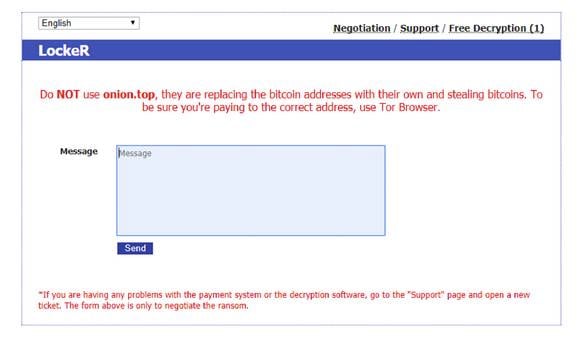
LockeR ransomware payment portal advising victims to avoid onion.top [Source: Proofpoint]
Bitcoin addresses associated with the diverted payments have raked in $22,000 so far.
Victims who pay out through this route will not be paying the crooks who are holding their files to ransom so they will not get their files decrypted even after a payment. This type of activity undermines the somewhat dubious trust relationship that underpins the ransomware business, Proofpoint said.
"While this is not necessarily a bad thing, it does raise an interesting business problem for ransomware threat actors and practical issues for ransomware victims," it adds.

Sigma ransomware payment domain as viewed with the Tor Browser (left) and via the .top Tor proxy (right) [Source: Proofpoint]
Ransomware-flingers are fighting back. For example, the Magniber ransomware appears to combat Bitcoin address replacement by splitting it into four parts in the HTML source code, making it harder for proxies to detect the Bitcoin address pattern. GlobeImposter ransomware urges users to use the Tor browser and hides the .onion payment address from the victims. "Instead of providing it as a link in ransom note, it is obfuscated in the note, and deobfuscated at run-time when the user clicks a button," Proofpoint said. ®
