This article is more than 1 year old
Android snoopware Skygofree can pilfer WhatsApp messages
Sophisticated nasty also able to listen in based on location
Mobile malware strain Skygofree may be the most advanced Android-infecting nasties ever, antivirus-flinger Kaspersky Lab has warned.
Active since 2014, Skygofree, named after one of the domains used in the campaign, is spread through web pages mimicking leading mobile network operators and geared towards cyber-surveillance.
Skygofree includes a number of advanced features not seen in the wild before, including:
- Location-based sound recording through the microphone of an infected device – recording starts when the device enters a specified location
- Abuse of Accessibility Services to steal WhatsApp messages
- Ability to connect an infected device to Wi-Fi networks controlled by the attackers
All the victims of the ongoing campaign detected so far have been located in Italy, leading Kaspersky to theorise that the developers are themselves Italian.
Kaspersky's researchers reckon the group may have filled the vacuum created by the demise of HackingTeam, following a 2015 breach in which the source code of commercial law enforcement surveillance/spyware tools that the firm developed was leaked, among other embarrassing secrets such as corporate emails.
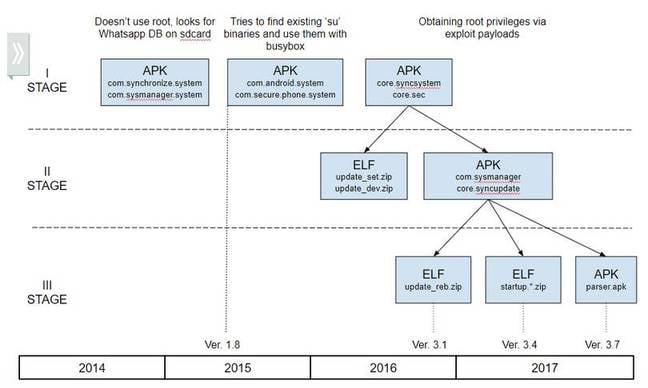
Skygofree is a strain of multi-stage spyware that gives attackers full remote control of an infected device. It has undergone continuous development since the first version was created at the end of 2014, Kaspersky Lab said.
"The implant carries multiple exploits for root access and is also capable of taking pictures and videos, seizing call records, SMS, geolocation, calendar events and business-related information stored in the device's memory," the firm added.
The malware is even programmed to add itself to the list of "protected apps" so that it is not switched off automatically when the screen is off, circumventing a battery-saving feature that might otherwise limit its effectiveness.
The attackers also appear to have an interest in Windows users. Researchers found a number of recently developed modules targeting Microsoft's OS.
"High-end mobile malware is very difficult to identify and block and the developers behind Skygofree have clearly used this to their advantage: creating and evolving an implant that can spy extensively on targets without arousing suspicion," said Alexey Firsh, Malware Analyst, Targeted Attacks Research, Kaspersky Lab.
"Given the artefacts we discovered in the malware code and our analysis of the infrastructure, we have a high level of confidence that the developer behind the Skygofree implants is an Italian IT company that offers surveillance solutions, rather like HackingTeam."
More information, including a list of Skygofree's commands, indicators of compromise, domain addresses and the device models targeted by the implant's exploit modules can be found in a blog post on Securelist.com.
Bootnote
Kaspersky Lab moved to clarify that Skygofree has no connection to Sky, Sky Go or any other subsidiary of Sky, and does not affect the Sky Go service or app.