This article is more than 1 year old
Leftover Synaptics debugger puts a keylogger on HP laptops
Vendor first to patch, expect other OEMs to follow
For the second time this year, HP Inc has had to patch its laptops after a security researcher found a driver-level keylogger – and this time, other laptop-makers might have to check their own products.
The debug trace was in the Synaptics Touchpad driver used almost across-the-board in HP laptops, and while it is turned off by default, a registry entry could turn it on. While few home users would be likely to turn it on, it would be a tasty exploit for RAT (remote access trojan) herders.
The bug was disclosed by "ZwClose", who was looking through the driver to see if they could adjust the backlighting of HP laptop keyboards.
A line in the SynTP.sys keyboard driver caught ZwClose's attention:
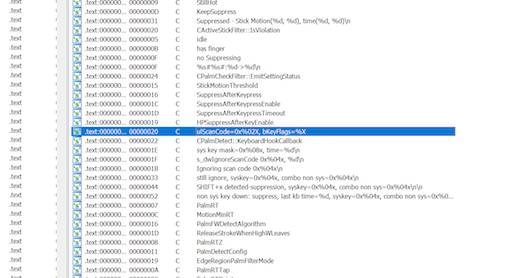
The revealing text: "uLScanCode=0x%02X, bKeyFlags=%X"
More digging showed that the driver "saved scan codes to a WPP trace" (Windows software trace preprocessor).
HP acknowledged the issue, and issued updates for more than 173 commercial products and over 293 consumer products.
ZwClose wrote that a fix would also land in Windows Update.
Consumer items still awaiting a fix include eight HP Envy variants, an HP Stream series, as well as an HP x360 11 convertible.
HP's advisory stated that the vulnerability "impacts all Synaptics OEM partners", so we can expect a rash of driver updates to be released in the future. HP added: "Neither Synaptics nor HP has access to customer data as a result of this issue."
Back in May 2017, security researchers from Swiss outfit Modzero found a keylogger in HP laptops' Conexant audio drivers. As with the latest discovery, the logging was in debugging code the developers forgot to remove from production models. ®
