This article is more than 1 year old
Equifax fooled again! Blundering credit biz directs hack attack victims to parody site
Tim on the social media team will need a new job
You'd have thought that Equifax staff would be on their toes ever since the megahack that exposed the private data of over 143 million Americans but the corporation's social media certainly haven't got the message.
When news of the hack was published on September 7, over a month after its scale had been discovered, Equifax set up a website for worried customers to check if they had been affected – equifaxsecurity2017.com – rather than setting it up on the equifax.com domain.
As a bit of fun security researcher Nick Sweeting set up securityequifax2017.com with a familiar look and feel, just like phishers do every day. To make that point the headline on the website was "Cybersecurity Incident & Important Consumer Information which is Totally Fake, why did Equifax use a domain that's so easily impersonated by phishing sites?"
Turns out he had a point, since the site fooled Equifax itself. Shortly after setting up the site, Equifax's official Twitter feed started to link to Sweeting's fake page and in a series of posts dating from September 9 Tim on Equifax's social media team began tweeting out the wrong URL to customers concerned about their data.
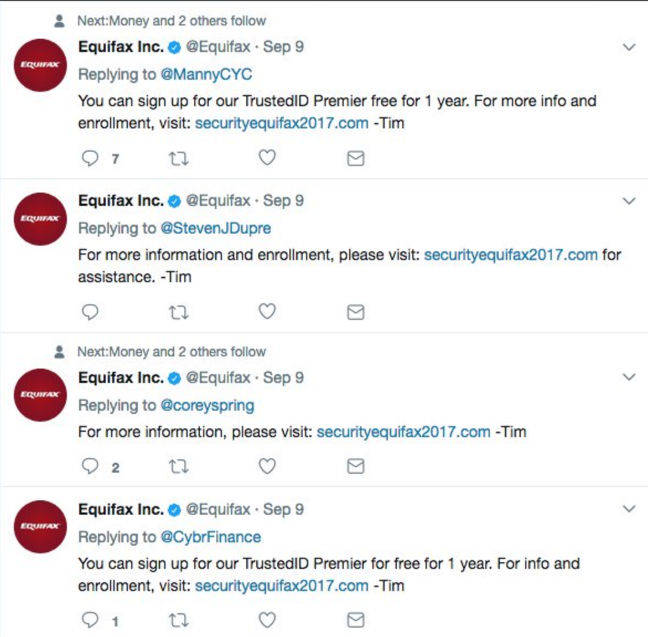
Seriously, Tim?
The tweets (now removed by red-faced Equifax staff) continued until Sept 18 before they were spotted by stanleyspadowski on imgur and @aaronkkruse on Twitter. It's not known how many people were directed to the site, and it has since been blocked by Google.
I'm now on the Chrome domain blacklist. Not particularly motivated to change the domain, so for now these screenshots are the legacy. https://t.co/Iznla9UvfK
— Nick Sweeting 🚲 (@thesquashSH) September 20, 2017
You might think that, given the long time Equifax had to prepare for the hacking announcement, it would have been on the ball. But instead the emergency website it set up for consumers to check their status was a slapdash job, it tried (and failed) to indemnify itself against litigation with legal trickery and took nearly a week to confirm how many UK citizens were caught up in the event.
The entire hack was possible because the company wasn’t patching promptly, having left an Apache Struts flaw unpatched for months – although Equifax is not alone in that. The company's CSO and CIO have since retired, presumably with a nice golden parachute, and the CFO and other senior management's share sales are being investigated.
Given that Equifax is trying desperately to avoid a full-scale investigation into its business practices, you'd have thought the company would have been more on the ball. It appears not. ®
