This article is more than 1 year old
SAP pushes 25 patches and two patch patches
HANA User Self Service isn't meant to give crims self-service, but it can. And you can plug it
Once you stop reeling from Microsoft's monster two-month patch dump, VMware's new patches and news that Dungeons & Dragons is going digital, brace yourself again because SAP has popped out has 25 patches and two patches for patches for you to consider.
The most severe, which SAP customers* can read about at Security Note 2424173, rank a 9.8 on the 10-point CVSS vulnerability assessing-scale. Here's why: SAP says the problem, which hits HANA's User Self Service feature “can allow an attacker to take control of the system.”
It's not an easy in. First you'll need to have turned on the User Self Service component that's off by default. Then you'll need to run it on an untrusted network. If you find yourself on the wrong side of those conditions, you're looking at either a patch or deliberate disablement to ameliorate matters.
SAP HANA extended application services have an 8.8-rated bug that “could allow an attacker to elevate privileges by impersonating another user in the system.”
There's also a “Remote Code Execution vulnerability in SAP GUI for Windows” that scores an 8.0 and a 7.2-rated update to an older Note concerning an SQL injection vulnerability impacting SAP Database Monitors for Oracle.
SAP also publishes some nice stats about the security of its products, as the graphs below show.
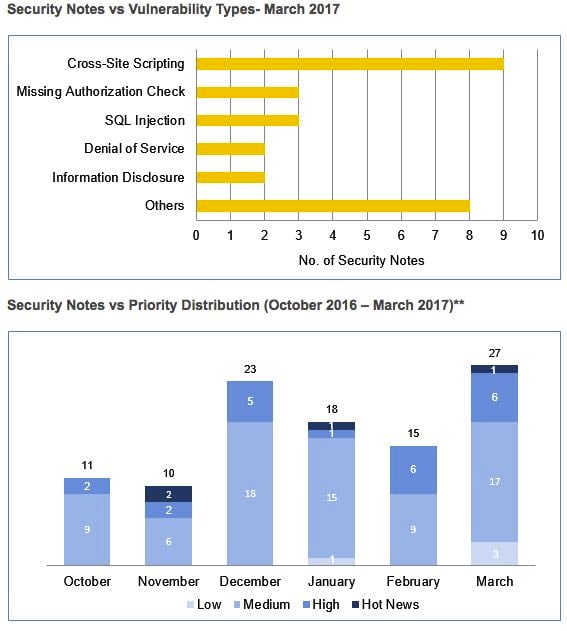
Those graphs show SAP's had a tricky month. So enjoy your patching, people. If nothing else this month will give you lots of practice at it! ®
*SAP's Security Notes require a logon to read, and those logons aren't handed out to world+dog.
