This article is more than 1 year old
It's 2017 and 200,000 services still have unpatched Heartbleeds
What does it take to get people patching? Not Reg readers, obviously. Other, silly people
Some 200,000 systems are still susceptible to Heartbleed more than two years and 9 months after the huge vulnerability was disclosed.
Patching efforts spiked after news dropped in April 2014 of the world's most well-known and at the time then most catastrophic bug.
The vulnerability (CVE-2014-0160) that established the practice of branding bugs lived up to its reputation: the tiny flaw in OpenSSL allows anyone to easily and quietly plunder vulnerable systems stealing passwords, login cookies, private crypto-keys, and much more.
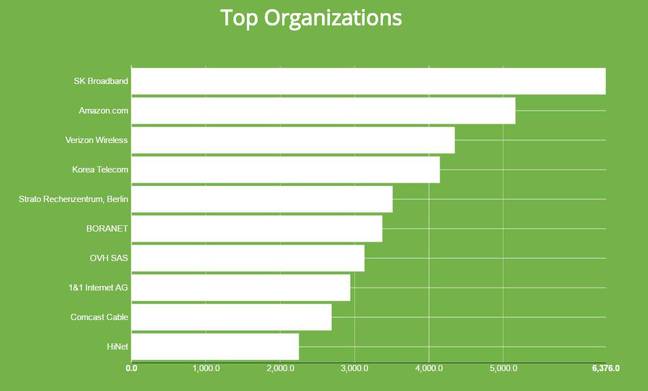
Shodan boss John Matherly says about 200,000 services remain Heartbleed-exploitable thanks to unpatched OpenSSL instances.
He found 42,032 services in the United States, 15,380 in Korea, 14,116 in China, and 14,072 exposed services in Germany.
About 75,000 of the vulnerable boxen bore expired SSL certificates, and ran Linux 3.x.
Nearly 3 years later and we're still looking at ~200,000 services vulnerable to Heartbleed: https://t.co/KU04PtWTJU pic.twitter.com/6mZhCUCVu6
— John Matherly (@achillean) January 22, 2017
A year ago one in 10 OpenSSL VPN servers were still vulnerable to Heartbleed.
Administrators are not only neglecting Heartbleed; as of May 2016 Stuxnet was the most common vulnerability (CVE-2010-2568) to hack stuff on the internet, according to Microsoft, despite that it had been widely disclosed for six years at the time Redmond revealed its numbers.
It gets worse; the most commonly exploited Microsoft Office vulnerability as of July 2016 only affects Office 2010, 2007 and 2003, indicating users had not upgraded their code, something even pirates had done.
Redmond warned the world in April 2015 that Word Macros had made a comeback then infecting half a million computers in what looks like a near-everlasting threat. Significant attack campaigns that relied on Word macros continued to appear throughout 2016. ®
