This article is more than 1 year old
Infected Android phones could flood America's 911 with DDoS attacks
One killer trojanised app or $100k of hardware is enough.
A research trio has shown how thousands of malware-infected phones could launch automated distributed denial of service attacks to cripple the US emergency phone system "for days".
The attacks are a new area of research and exploit the need for emergency call services to accept all calls regardless of origin.
The theoretical attack uses malware to mask a phone's International Mobile Subscriber Identity (IMSI) showing only the International Mobile Station Equipment Identity (IMSEI) numbers which cloaks the origin of attacks and frustrates identification and blacklisting efforts.
Negev Ben-Gurion University researchers Mordechai Guri, Yisroel Mirsky, and Yuval Elovici say the malware could place calls without alerting users.
They say in the 911 DDoS: Threat, Analysis and Mitigation [PDF] that 6,000 infected smartphones in a local area would jam an emergency call system.
The current United States Federal Communications Commission (FCC) regulations require that all emergency calls be immediately routed regardless of the caller’s identifiers," the researchers say.
"A rootkit placed within the baseband firmware of a mobile phone can mask and randomise all cellular identifiers, causing the device to have no genuine identification within the cellular network.
"Such anonymised phones can issue repeated emergency calls that cannot be blocked by the network or the emergency call centers, technically or legally."
Half of all mobile phone emergency callers would give up when an army of 6,000 infected phones were jamming 911 public safety answering points (PSAPs). This rises to 90 percent with 50,000 compromised handsets blasting the emergency line.
A fleet of 200,000 infected handsets could jeopardise emergency services across the entire US.
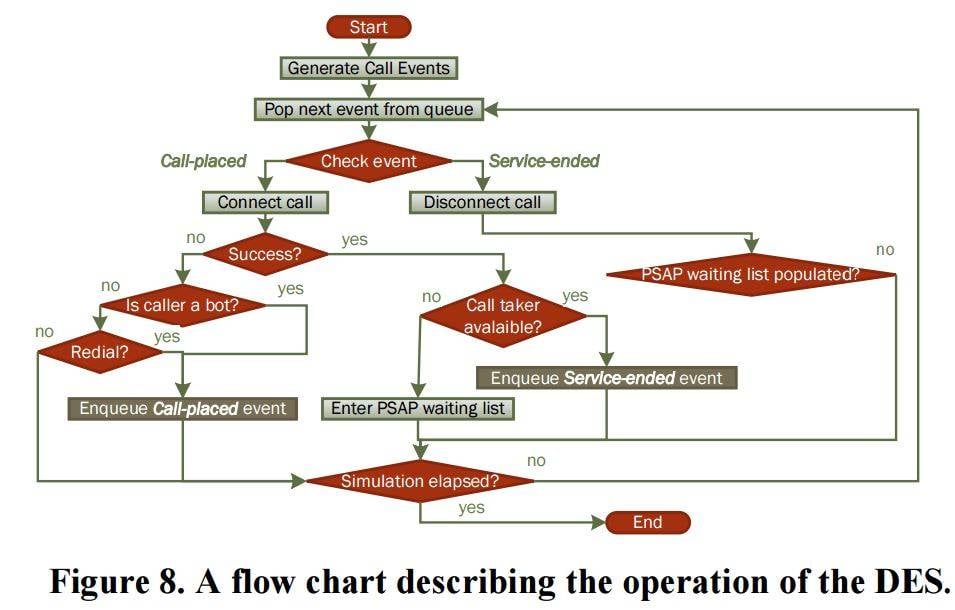
The hackers used a discrete event simulator (DES) and a handful of Samsung phones to test their work, noting that malware residing in a phone's baseband would push phones into a "no SIM" state, exposing only the IMEI number which is hard to track.
The team suggests the attacks can be prevented by storing IMSI numbers in a phone's trusted memory region, such as Android Pay, preventing alteration.
"We believe that the contributions of this paper will assist the respective organizations, lawmakers, and security professionals in understanding the scope of this issue and aid in the prevention of possible future attacks on the 911 emergency services," the authors conclude. ®