This article is more than 1 year old
Hackers turn to angr for automated exploit discovery and patching
Fuzzing and Driller all killer, no filler
Nullcon A team of researchers are battling to trouser the US Defense Advanced Research Projects Agency's US$2m prize to build a system that aims to best human offensive and defensive security personnel at exploitation discovery and patching.
The Shellphish team, with hackers in the US, France, China, Brazil, and Senegal, is big in the capture-the-flag circuit and won the DEF CON competition in 2006.
And so it jumped when DARPA in 2014 pinned the word "cyber" to the title of its then decade-old Grand Challenge competition and the quest to automate vulnerability discovery and remediation.
The agency tasked the information security industry with developing an autonomous exploitation discovery and patching system that could rumble with the real world.
This kicked off in June last year, with seven teams including Shellphish qualifying for the finals, which will be held at the popular DEF CON hacking conference in Las Vegas this August.
Shellphish's angr framework exploited an impressive 44 from 131 binaries and bagged US$750,000 along with other qualifying teams.

Those that succeed will score US$2 million for first place, US$1 million for second, and $US750,000 for third spot. The winning team will then compete against a crew of human hackers in a man vs machine race to find and patch vulnerabilities.
Flow
"Let's hope the humans win or we will have big problems," University of California, Santa Barbara member Antonio Bianchi says.
"We need to develop a system that will be fed programs and without human intervention will find vulnerabilities, exploit, and patch them."
Teams will perform with a cluster of 1280 cores, 16TB of RAM, and 128TB of storage.
An exploit in DARPA's book is input that causes a crash such as a segmentation fault.
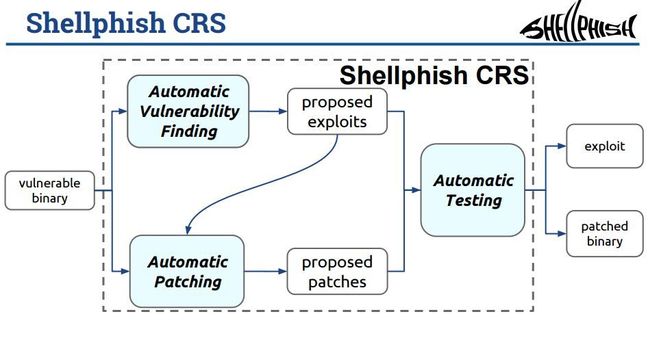
The self-described "rag-tag hackademic group"-cum-multimillion-dollar DARPA money-seekers developed the open source angr binary-analysis framework to be demonstrated to hackers at the Nullcon hacking conference in Goa, India.
It will use coverage-guided fuzzing and symbolic execution in a bid to find crashes. It combines the two in a system blending augmented fuzzing through selective symbolic execution, dubbed Driller and fully described in the paper Driller: Augmenting Fuzzing Through Selective Symbolic Execution, published at the Network and Distributed System Security Symposium conference last month.
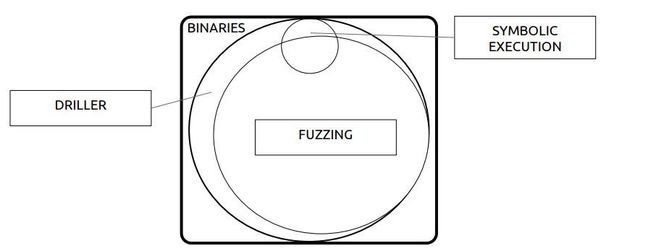
It can be used by others to help find and fix holes, however, and is available on Github.
The framework is flexible since it focuses on static and dynamic symbolic analysis, and is composed of smaller multiple open source projects:
- An executable and library loader: CLE
- A library describing various architectures: archinfo
- A Python wrapper around the binary code lifter VEX: PyVEX
- A VEX simulation engine: SimuVEX
- A data backend to abstract away differences between static and symbolic domains: Claripy
- The full-program analysis suite itself: angr
- A GUI for some features of angr: angr-management. ®
