This article is more than 1 year old
Hardsploit: The handy hacker help for hapless hopeful hardware hacks
Like Nessus, for Things. Because there's password gold in them thar chips
Nullcon Penetration testers Julien Moinard and Gwénolé Audic have produced a security testing framework to automate vulnerability scans for Things used on the internet of things.
The Hardsploit project, to be showcased at the NullCon security conference in Goa, India, is badged as an all-in-one hacking tool for hardware security audits that aims to become “the Nessus of hardware security”.
Nessus is a popular and easy-to-use automated software vulnerability scanner.
Moinard and Audic of Opale Security say hardware experts rather than security folk are typically the only people to audit embedded devices because they understand the complex protocols while penetration testers do not.
Hacking hardware should not be dismissed by software security experts, the pair say, because it can yield cleartext passwords, filesystems, and firmware.
Hardsploit stands to make that feat easier for those not in the know.
“The gap between software and hardware security has widened since the early 2000s … because hardware is mainly just a way to gain access to software,” Audic says.
“I am a software guy and guys like me should be able to access the hardware without struggling with a lot of documentation and to know everything about electronics.”
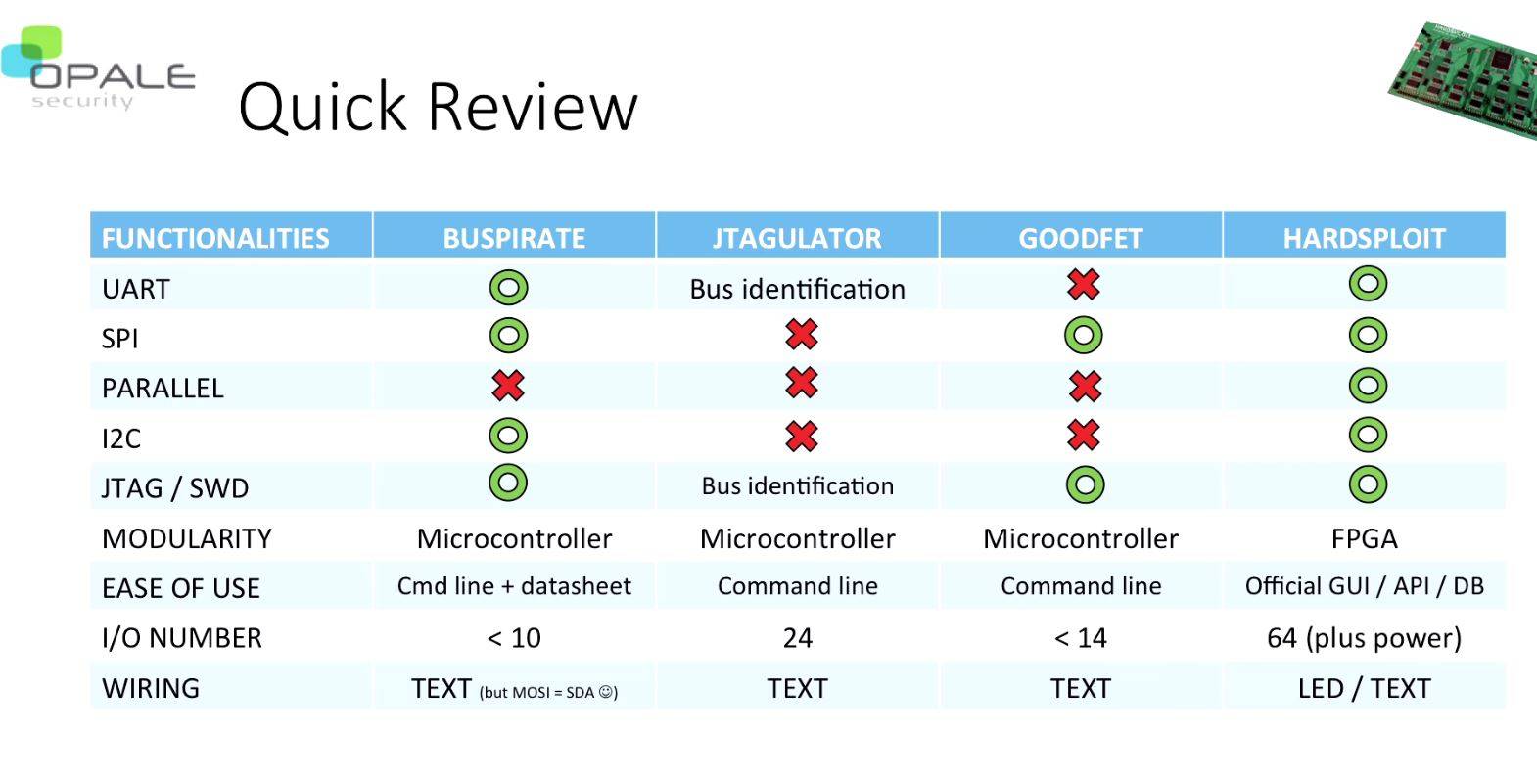
The pair says devices will use at least one communications bus, from I²C, to JTAG, SPI, PARALLEL, or UART in their chips regardless of internet connectivity. The technical idiosyncrasies of each makes hardware a challenge to audit more for many software security testers.
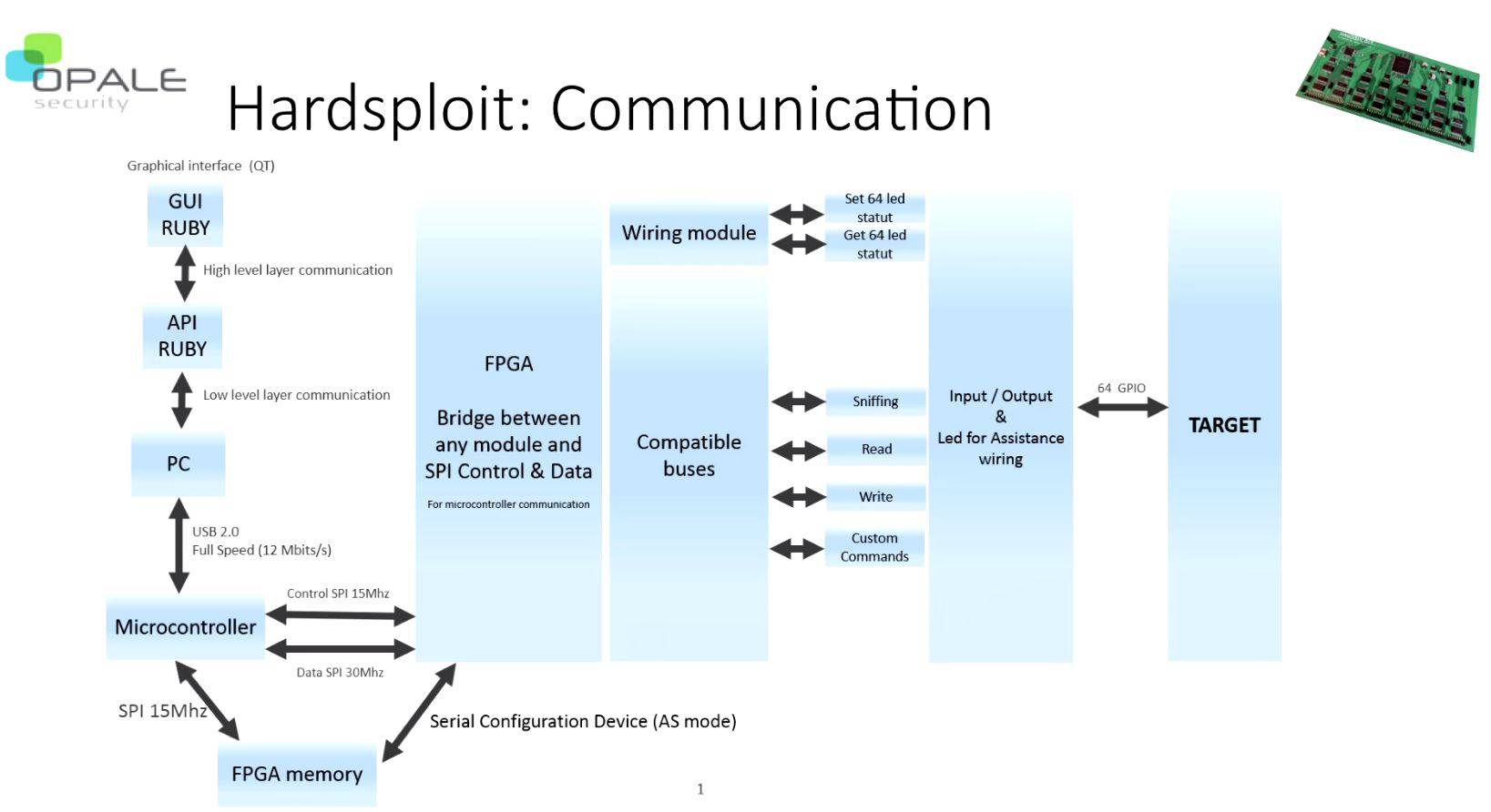
“The goal is to create a bridge between the hardware and the software … most of the time pen testers know how to access software but when you have hardware then it is more complicated,” Moinard says.
Attackers are attracted by the lack of security analysis and missing controls like firewalls and antivirus within embedded devices, and as a result are targeting hardware Moinard says.

Hardsploit
Hardsploit sports a graphical interface, sniffer, scanner, proxy, and memory dump, 64 I/O channels, a Cyclone II FPGA, USB 2.0, and measures 200mmx 90mm.
Assisted visual wiring and LEDs helps hackers plug the right wire into the correct socket.
Early prototype versions of the system involved lots of ducktape, zip ties, and a “slightly modified” (read mutilated) microwave oven.
Moinard says the software element will integrate with the Metasploit testing framework and will plug into other software APIs in the future. ®