This article is more than 1 year old
Trustworthy x86 laptops? There is a way, says system-level security ace
ARM isn't the answer either, adds Joanna Rutkowska
Smash the state
A nightmare scenario is malware managing to store secrets hidden away from the user in a persistent manner, so wiping the hard disk won't get rid of it. One way to do this is to smuggle it into flash storage on the motherboard chipset, storage reserved for firmware code.
“Imagine I have malware which might only be stealing my disk encryption key,” said Rutkowska, “and it can store it somewhere on the disk or on SPI Flash, or maybe on the Wi-Fi firmware, or maybe on the embedded controller firmware.”
If this were to happen, an attacker who seized the machine could instruct the hidden malware to unlock the computer and give up the swiped key to decrypt the data. “Game is over,” said Rutkowska.
There is a means of changing that game, however: a stateless laptop.
Rutkowska explained the core thesis of her December paper was to make it a requirement for laptop hardware to be stateless; that is, lacking any persistent storage: "This includes it having no firmware-carrying flash memory chips. All the state is to be kept on an external, trusted device. This trusted device is envisioned to be of a small USB stick or SD card form factor."
This external device was dubbed “trusted stick” by Rutkowska, “for lack of a more sexy name.” It is where the firmware, platform configurations, and the system and user partitions would be held in “a simple FPGA implemented device."
As such, said Rutkowska, “even if malware found a weakness in the chipset, allowing it to reflash the BIOS — and we have seen plenty of such attacks in recent years — it would not be able to succeed.”
However, Rutkowska's December paper noted it was unclear if Intel ME “would be happy when being put into an environment where the SPI flash it gets access to is externally forced to be read-only.”
This clean separation of state-carrying vs. stateless silicon is, however, only one of the requirements, itself not enough to address many of the problems discussed in the [October paper]. There are a number of additional requirements: for the endpoint (laptop) hardware, for the trusted “stick”, and for the host OS.
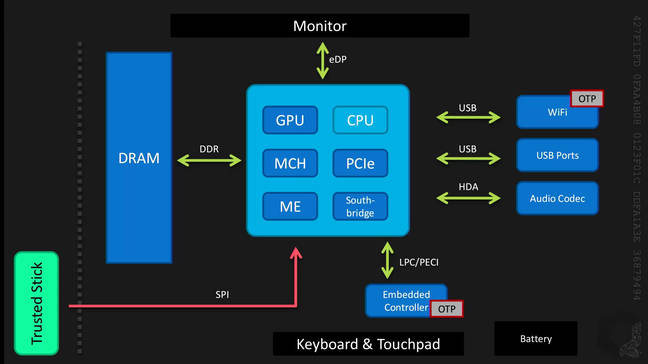
Joanna Rutkowska © 2015
Rutkowska said the creation of a stateless laptop might not even be that difficult. The most simple implementation, as displayed above, simply removes the SPI Flash and places it on the trusted stick, alongside removing the disk, and ensuring the discrete devices are using one-time programmable memory instead of flash. More complicated versions were suggested, which Reg readers may find in the recording of the talk.
What would remain in all these implementations, however, is ME. The security expert suggested "a hypothetical rootkit in ME" would be capable of leaking sensitive information through networking, even if it were prevented from residing on the laptop's states.
Making a distinction between what she called "classic" and "sophisticated" malware, the researcher then took the audience through an array of scenarios in which the sophisticated malware attempted to covertly leak information, rather than transparently "establishing a TCP connection to nsa.gov."
Scenario 0 was an air-gapped system: "If the computer is not inside a Faraday cage, there [are] still plenty of other networks or devices around it. Which means that ME can theoretically use your Wi-Fi card, or even speaker to establish a cover channel with, say, your phone."
Rutkowska stated kill-switches would be required for any transmitting devices in order to truly air-gap any system containing ME, though "apparently that may not even be enough" as covert side-channels have been demonstrated which used power or temperature fluctuations to leak information.
Scenario 1 was a closed network of trusted nodes: "We assume that all of these nodes are trusted, by definition allowing all of these nodes may compromise anybody else." In this scenario, even though each peer would retain the malicious ME microcontroller, ME would be connecting to the processor through a proxy which could potentially be tunneling any leakage from ME, and so a malicious ISP would be unable to retrieve these secrets.
While ME could theoretically modulate its packets to provide another covert side-channel in this example, Rutkowska stressed that this would be "extremely difficult" for ME to implement.
Scenario 2 used an "open network via Tor/VPN" when connecting with anybody, not just a trusted computer. Here the proxy – which could be implemented within the embedded controller thanks to the trusted stick – would, even when the user is connecting with an untrusted website, prevent against leakage from ME to a malicious part of the communications infrastructure.
How may one prove that one has a truly stateless laptop? Rutkowska acknowledged "this comes down to the problem of how do we compare two different printed circuit boards (PCBs)?" and lamented that industry currently had no way to compare two different PCBs and confirm they looked identical.
While a diff tool that analyses photographic inputs may only provide a comparison of the PCPs' geometry and not the internal status of the chip, Rutkowska stated it would provide a tremendous increase in difficulty for vendors who were attempting to contribute malicious modifications to the PCPs.
But don't give up
"Many people say that perhaps we should all give up on x86, because of ME for example," Rutkowska told congress attendees, who applauded in response. "Yet this is not such a silver bullet."
Rutkowska dismissed the ARM architecture as an alternative, commenting that "there is no such thing as an ARM processor. ARM just sells IP, and then there are vendors such as Samsung who take this IP and design their own system on a chip. This is still a proprietary processor which will contain whatever they want."
The researcher added that there was nothing preventing vendors from modifying ARM's TrustZone to create ME-like technology.
The use of open hardware processors was a better alternative, suggested Rutkowska, such as FP GA-implemented processors – potentially manufactured on 3D printers allowing owners to control exactly what the hardware consists of, although this is "probably not coming for 10 or 20 years " – but meanwhile the performance and lack of security technologies prevents this from becoming a viable solution for the next five years, reckoned the researcher. Even then, such a clean separation of states would make sense as per the vulnerabilities Rutkowska already discussed.
"Even now, some of you may say, 'Yeah, that's a cool idea, but the market may be into that.' right?" concluded Rutkowska, echoing a speech GCHQ's director general Robert Hannigan delivered earlier this year blasting the free market's ability to ensure public security.
Drawing a parallel between the development of human rights and the development of secure personal computers, Rutkowska suggested legislation may come to the rescue. ®
