This article is more than 1 year old
Free HTTPS certs for all – Let's Encrypt opens doors to world+dog
And it's pretty easy to install via a command line
How-to The Let's Encrypt project has opened to the public, allowing anyone to obtain free TLS certificates and set up HTTPS websites in a few simple steps.
It's a major leap forward in encrypting the world's web traffic, keeping people's information and browser histories out of the hands of eavesdroppers and and other miscreants.
The certification-issuing service is run by the California-based Internet Security Research Group (ISRG), and is in public beta after running a trial among a select group of volunteers. The public beta went live at 1800 GMT (1000 PT) today.
Its certificates are trusted by all major browsers – Google Chrome, Mozilla Firefox and Microsoft's Internet Explorer worked in our office with fresh certs from the fledgling certificate authority.
Incredibly, it is almost too easy to use. You download an open-source client to your web server, and then one command will request and install a certificate, and configure your system to use it. And that's it.
Here's what this humble hack ran on a personal webapp development machine powered by Apache (yeah, yeah, kicking it old school):
cd ~/src git clone https://github.com/letsencrypt/letsencrypt.git cd letsencrypt ./letsencrypt-auto --apache -d your.domain.here
You're then prompted for your sudo password. Next, the client installs its dependencies, and then asks for your email address so you can be contacted if there are any problems. You're also asked to agree to a set of terms and conditions. Next, it asks if you want to force all traffic to go through HTTPS – yes, obviously.
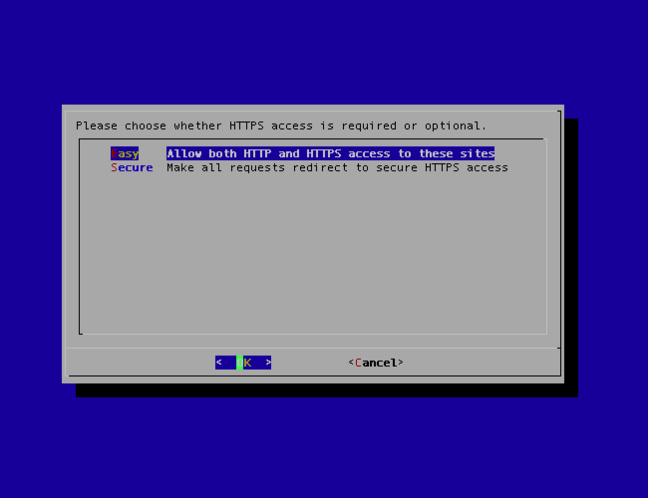
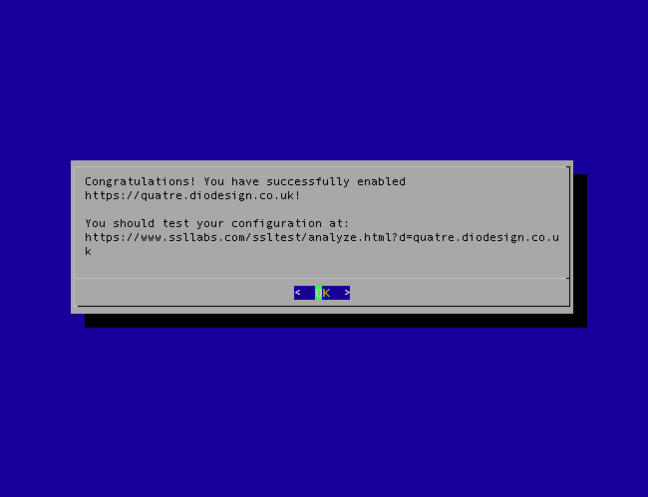
And then, bam. It's done. A 2048-bit RSA TLS 1.2 certificate with a SHA-256 signature installed and the server configured to use it. The cert gets an A from Qualys SSL Labs.
Crucially, this process can be completely automated – email addresses and agreement to the fine print can be set on the command line using --email and --agree-tos. This is especially important because you'll need to renew the certificates every 90 days, so it's probably best to do that automatically.
Full documentation is here and a quick start guide is here. The project's root certificates and intermediate certificates can be found here; the intermediates are cross-signed by IdenTrust.
Let's Encrypt is overseen by folks from Mozilla, Akamai, Cisco, Stanford Law School, CoreOS, the EFF and others, and sponsored by various internet organizations.
"It’s time for the Web to take a big step forward in terms of security and privacy. We want to see HTTPS become the default. Let’s Encrypt was built to enable that by making it as easy as possible to get and manage certificates," the team wrote in a blog post today. There's a reward going for anyone who can find a security hole in the service.
"We have more work to do before we’re comfortable dropping the beta label entirely, particularly on the client experience. Automation is a cornerstone of our strategy, and we need to make sure that the client works smoothly and reliably on a wide range of platforms. We’ll be monitoring feedback from users closely, and making improvements as quickly as possible."
Let's Encrypt's client software emerged in early November, and signed its first certificate in September. Since then the team have been squishing bugs in their systems, managing to catch at least one nasty flaw before going public.
You can typically expect to pay for SSL certificates, although some authorities do offer freebies. None so far, to our knowledge, are as straightforward as Let's Encrypt's free service. ®
