This article is more than 1 year old
Google to shell out up to $58k for new Nexus epic pwnage
Remote low level attacks plus patch to be answered with cash
Researchers can score up to US$58,000 for bypassing core Nexus security mechanisms with a remote exploit under an expansion of Google's bug bounty program launched today.
The top payments under the Security Rewards program are for bypasses of controls that Google uses to minimise exploitation risks.
Hackers can land the most cash by compromising the Android TrustedZone or Verified Boot using a remote attack through an installed app, attracting bonuses of US20,000 and US30,000 respectively.
Security engineer Jon Larimer says the rewards are for Nexus devices currently on sale including the Nexus 6 and Nexus 9 as of the time of writing.
"For vulnerabilities affecting Nexus phones and tablets available for sale on Google Play, we will pay for each step required to fix a security bug, including patches and tests," Larimer says
"In addition to rewards for vulnerabilities, our program offers even larger rewards to security researchers that invest in tests and patches that will make the entire ecosystem stronger.
"The largest rewards are available to researchers that demonstrate how to work around Android’s platform security features, like ASLR (address space layout randomisation), NX, and the sandboxing that is designed to prevent exploitation and protect users."
The Choc Factory claims to be the first to offer a bug bounty for a "major" phone device line.
Security bods will score a variety of payments between $333 to $8000 for low test case bugs to critical proven vulnerabilities that are coupled with patches.
Those offering Google a means to fix flaws will double the payment.
Skilled hackers who pop the Nexus kernel will land an additional will gain $10,000 on top of their rewards and a further $20,000 for pulling off the attack remotely.
Hackers need not apply if their bugs merely crash apps, require complex user interaction, phishing, or tap-jacking.
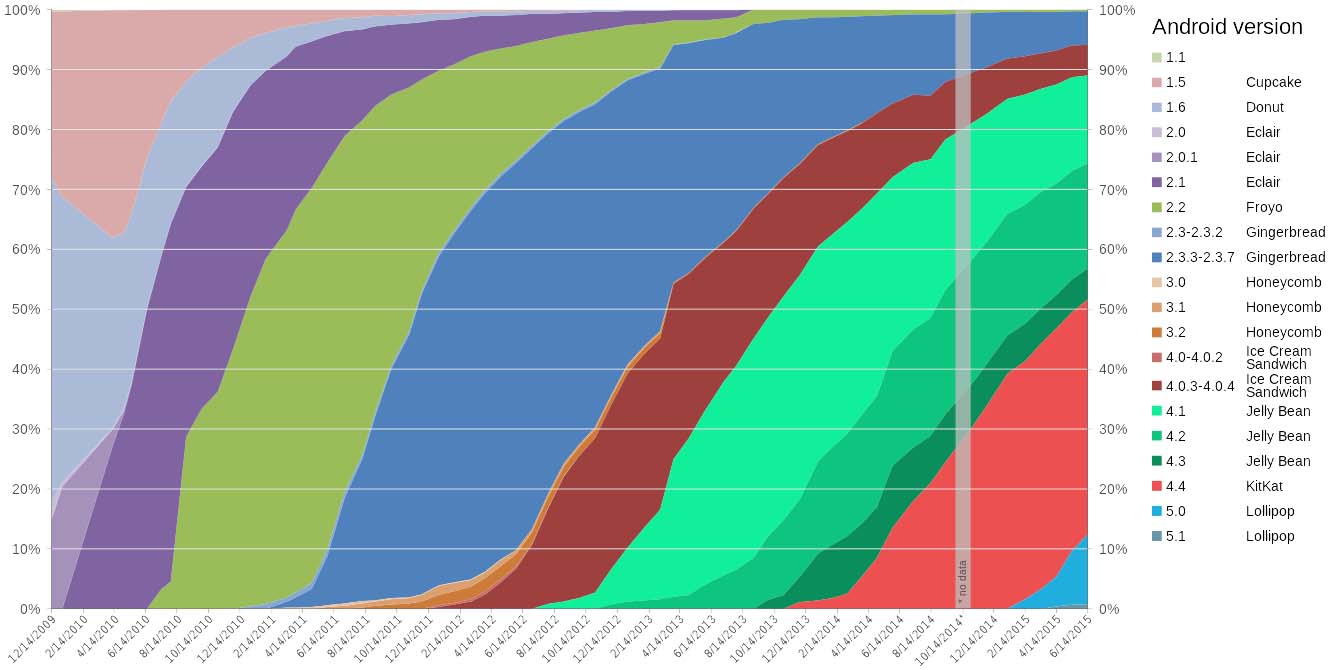
While Google will go to some length to fix flaws, the patches are often slow to reach users, if they ever see the light of day. Almost 40 percent of users run the outdated Android KitKat platform and therefore rely on telcos to distribute over-the-air updates.
Custom ROMs can be installed for manual upgrading but the process is too complex and occasionally unstable for most users.
Contrast Security chief technology officer Jeff Williams says the bug bounty program is an effective means to reduce security issues but adds that a 'dramatic' change to the software distribution is required.
"These programs are affordable and has clearly proven effective for a broad range of companies," Williams says.
"The Android ecosystem is extremely complex, with many different versions from a wide variety of vendors. Long term, I don’t see this program or any other security program being effective without some dramatic changes to the way this software is distributed." ®