This article is more than 1 year old
VXer fighters get new stealth weapon in war of the (mal)wares
Foiled traditional systems force white hats to bare metal
A bare-metal analysis tool developed by University of California researchers promises to help tip the battle between virus writers and black hats by cloaking malware investigation efforts.
The tool is the latest weapon in the war between the diaspora of independent and vendor malware researchers and their VXer foes. Their rolling brawl has given rise to advanced cloak and dagger tactics employed by both belligerents.
Black hats have developed impressive methods to find technical artifacts that help them to distinguish between infected computers belonging to victims and and those malware researchers create to detect and foil attacks.
Once known, the means to detect such artifacts is coded into the next generation of malware allowing it to appear harmless in the eyes of security researchers and anti-virus vendors.
Malware coded in this way would then be immune from probes on given sets of malware analysis platforms, allowing more victims to be plundered before anti-virus systems crash the party.
Virus writers detected researchers' analysis platforms through a number of methods including fingerprinting the runtime environment for certain registry keys, function hooks and background processes.
They could also determine if a virtual operating system was used for analysis by way of variations in execution.
Public and even private malware analysis platforms could be fingerprinted if vxers with access to the engines uploaded wares designed to harvest environmental artifacts.
While the Vxers hid, the white hats sought them out. Malware was commonly splashed across a host of detection environments in often failed hopes to find one that would not cause it to clam up.
So-called transparent analysis systems were the latest productions from the white hats which aimed to replicate victim bare-metal computers. It left fewer artifacts for the vxers to find but were so resource-intensive that it ground important fine-grained analysis to a halt. BareBox, one such system, worked by partitioning the host's physical memory for malware analysis and subsequent re-imagining, but it could be detected by the more advanced wares.
Other bare-metal boxes including Nvmtrace were limited in the information they could extract from analysed malware.
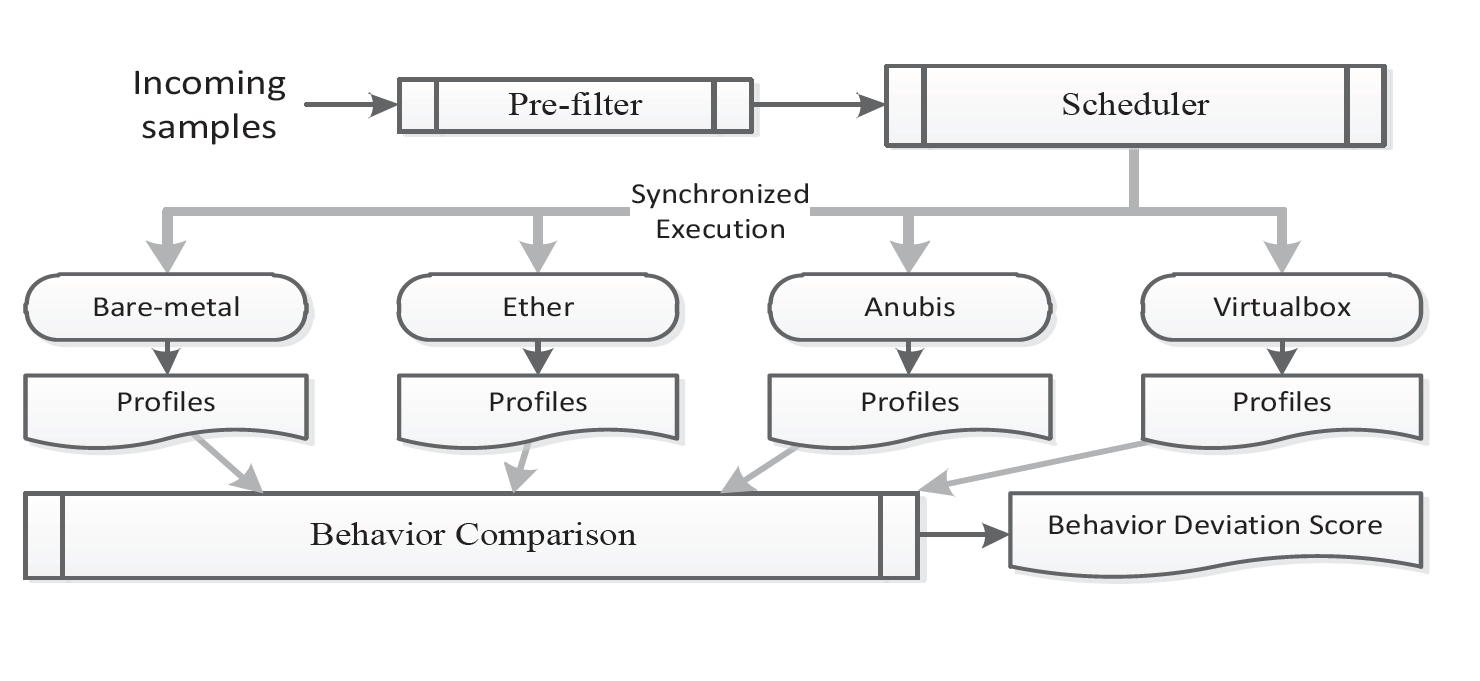
Now Dhilung Kirat (@Dhilung), Giovanni Vigna, and Christopher Kruegel have developed the latest white hat weapon that analysed malware by deploying it across bare-metal and traditional emulated environments.
In tests using the popular Ether, Anubis and Cuckoo Sandbox environments, the BareCloud platform detected 5835 evasive malware instances from 110,005 recently crafted malware samples.
"The ultimate way to thwart such detection is to analyse malware in a bare-metal environment," the trio wrote in the paper BareCloud: Bare-metal Analysis-based Evasive Malware Detection to be presented at the upcoming Usenix 14 conference.
"The disk-level activity is extracted by comparing the system's state after each malware execution with the initial clean state.
"Using the understanding of the operating system of the analysis host, BareCloud also extracts operating-system-level changes, such as changes to specific registry keys and system files."
BareCloud also introduced a novel evasion detection approach based on hierarchical similarity-based comparison which the authors said produced better results than existing methods.
It could detect any attempts by malware to make persistent changes to systems or contact command and control servers - feats the wares would need to pull of in order to be damaging, the writers said.
The trio, who work under sponsorship from the US Army and Navy, will now focus on making the bare-metal component of their system more transparent and on building an iSCSI module to provide richer file system-level event tracing through the extraction of high-level intermediate file system operations. ®