This article is more than 1 year old
We told you jailbreaking your iThing was dangerous
Ad revenue looted from 75,000 infected iOS fondelslabs
Chinese malware has infected more than 75,000 iPhones and hijacked some 22 million advertisements and stealing revenue from developers on the iOS jailbreak community, virus prober Axelle Apvrille says.
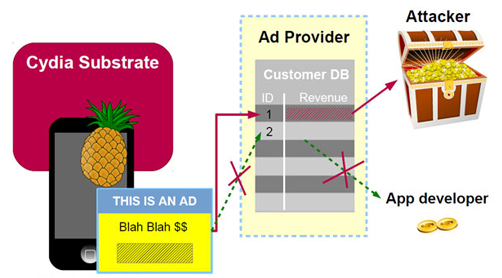
The AdThief malware relied on the Cydia Substrate extension present only on jailbroken Apple devices to hijack advertising bucks. Unmodified ithings are safe.
Apvrille located and confronted a Chinese vxer Rover 12421 who admitted writing the AdThief code but denied propagating it.
She explained in a paper Inside the iOS/AdThief malware [pdf] that advertiser identities were changed so that revenue was redirected to attackers.
"In other words, each time you view or click an ad on an infected device, the corresponding revenue goes to the attacker, and not to the developer or the legitimate affiliate," Apvrille (@cryptax) said.
"[AdThief] hooks various advertisement functions and modifies the developer ID (promotion ID) to match that of the attacker."
It targeted 15 mobile advertising kits including Google Mobile Ads and Weibo, four of which were based in the US, two in India and the remainder in China. The targets were identified because the attacker forgot to remove identifying information from the code.
A further gaffe meant strings included the path '/Users/Rover12421' allowing Apvrille to identify the coder who ran a blog detailing various Android hacks, a Github and inactive Twitter account.
Apvrille said while 75,000 infected devices was small compared to the scores of iOS devices in use, attackers likely made bank with an estimated 22 million ads hijacked.
"... the malware has probably had a fair amount of impact and generated significant revenue for the owners."
Malware targeting Android was far more common since the security controls both on the devices and Google's Play app store were more lax than Cupertino's iOS portfolio.
Users insisting on jailbreaking their devices to make use of pirate apps the Cydia store should change their device's root password, set by default to 'alpine'.®