This article is more than 1 year old
Network hijacker steals $83,000 in Bitcoin ... and enough Dogecoin for a cup of coffee
Wow. Such hack. Very router. So BGP. Wow.
Researchers at Dell's SecureWorks Counter Threat Unit (CTU) have identified an exploit that can be used to steal cryptocurrency from mining pools – and they claim that at least one unknown miscreant has already used the technique to pilfer tens of thousands of dollars in digital cash.
The heist was achieved by using bogus Border Gateway Protocol (BGP) broadcasts to hijack networks belonging to multiple large hosting companies, including Amazon, Digital Ocean, and OVH, among others.
"In total, CTU researchers documented 51 compromised networks from 19 different Internet service providers (ISPs)," the Dell team wrote in a blog post on Thursday.
By broadcasting malicious network routes via BGP, the attacker was able to redirect traffic from legitimate currency-mining servers on one network to bogus servers on another network that masqueraded as the genuine article.
These spoofed mining servers allowed clients to keep mining cryptocurrency but they never issued any payouts. All proceeds from the mining activity instead went straight into the attacker's pockets.
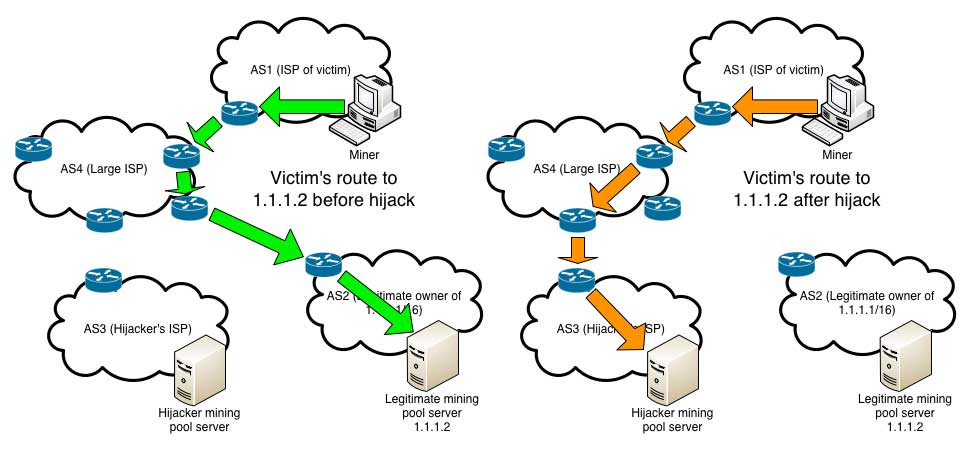
Using BGP, attackers diverted traffic from the correct route (left) to a spoofed mining server (right)
Source: Dell SecureWorks (Click to enlarge)
The Dell researchers say these attacks took place over a sustained period between February and May 2014, and by their estimates, the attacker was able to make off with approximately $83,000 in cryptocurrency.
Obviously, most of that was probably Bitcoin, since it's the only crypto-cash with any significant real-world value. As of Thursday, a single Bitcoin was worth around $590. But the Dell team says Bitcoin wasn't the only currency that was skimmed.
"The threat actor hijacked the mining pool, so many cryptocurrencies were impacted," the researchers write. "The protocols make it impossible to identify exactly which ones, but CTU researchers have mapped activity to certain addresses."
One miner the researchers interviewed said he estimates he lost around 8,000 Dogecoins during one hijacking incident toward the end of March. According to Dogepay.com, such a haul would be worth $1.53 in today's real-world dollars.
The Dell researchers eventually traced the bogus BGP broadcasts to a single router at an unnamed Canadian ISP, but no culprit in the attacks has been identified.
While the hijacking attacks were real and victims lost crypto-coins that could be traded for real money, however, the Dell team says the risk of future such attacks is "minimal."
"Unlike network routing protocols that can automatically initiate a connection from one network, both ends of BGP-connected networks (also known as a 'peers') must be manually configured to communicate," the researchers write. "This requirement ensures malicious networks cannot hijack traffic without human intervention from a legitimate network."
In fact, the SecureWorks CTU says two likely possibilities in the attacks they observed are that a rogue employee of the Canadian ISP was responsible, or that a former employee was able to compromise a router using an old password.
The researchers say one way that ISPs can avoid falling prey to malicious BGP broadcasts today is to opt in to the Resource Public Key Infrastructure (RPKI) service, which uses cryptographic certificates to verify the origins of network messages.
Cryptocurrency miners, on the other hand, have an even easier solution available: they can require their mining pool servers to use Secure Socket Layer (SSL) encryption, which prevents connections from being rerouted to another server, even if that server has the same IP address as the legitimate one. ®
