This article is more than 1 year old
iSense something, a presence not felt since... Apple sketches fanboi-finding infrared sensors
Patent application covers tech to detect man from machine
Apple hopes to patent a gizmo that uses heat and infrared light to know when you're nearby.
The US Patent and Trademark Office (USPTO) has published an application, titled Infrared Sensors for Electronic Devices, drawn up the company that describes technology which would use infrared to detect the presence of something and temperature readings to distinguish between a living body and an inanimate object.
The sensors, writes Apple, could then be used by software to tell when a person is handling a device and perform actions accordingly, such as waking up from sleep mode or performing action.
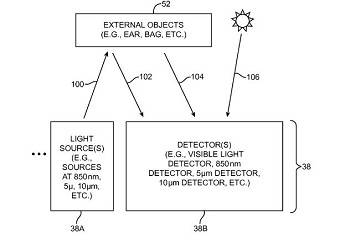
Apple's patent ... how the sensors could work
"Using sensors that measure the temperature of external objects such as a user's head, that measure the proximity of nearby objects, that measure ambient light levels, and/or that measure motion in objects such as a user's hand, control circuitry can control the operation of an electronic device," the company said in the application.
"For example, the functionality of the electronic device may be controlled based on how far the electronic device is located from external objects such as a user's head."
Based on the filing, it's not hard to imagine an iPhone or iPad that could automatically turn on its screen when the user moves to pick the device up, or prevent waking up from accidental button presses occurring when the device is being carried in a pocket or bag.
Applications of the technology, said Apple, could range from notebooks and tablets from handsets and other devices.
Those anxious for the much-rumored iWatch release may also want to take note of the filing as Apple also mentions "somewhat smaller portable devices such as wrist-watch devices," perhaps further suggesting an imminent watch release.
It is always worth noting, however, that patent applications are just that – applications. They do not necessarily indicate that a technology is being used in a prototype, let alone integrated into a production-ready device. ®
