This article is more than 1 year old
Cryptome pulled OFFLINE due to malware infection: Founder cries foul
'Craven and shallow technical justification' for censorship, fumes whistleblower
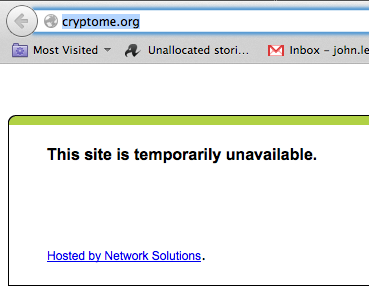
Updated Whistle-blowing site Cryptome has been left temporarily unavailable after its service provider NetSol stopped routing traffic towards the site following the discovery of a suspect and probably malicious PHP file.
Cryptome's John Young criticised NetSol's decision on to pull the plug on the whistle-blowing site as an overreaction to a minor problem which he claimed had been quickly resolved.
He accused Webcom and Network Solutions of effectively censoring the site "using craven and shallow technical justifications" in a barbed and characteristically combative blog post.
Cryptome sees the Web.com and NetSol suspension of Cryptome.org without prior notice to be as illegal and vicious as an attack by government, corporation, hacker or spy...Use of technical rationales to unpremeditatedly attack and censor are now commonplace by telecommunications providers... This is an instance of that violation of customer trust.
Young's anger appears focused on NetSol's supposed inability to reactivate the site for up to 48 hours after the removal of the offending file as well as its decision to temporarily suspend Cryptome "without prior notice".
"Nothing was sent before then about the file, that it should be removed or that a suspension would occur," Young blogged. "By time the email was read the site was shut. Immediately after reading the email the PHP file was removed by FTP and a response to NetSol was emailed reporting the removal."
Keeping Cryptome up and running is a fairly thankless task that's regularly fraught with difficulties. Microsoft filed a DMCA notice of copyright violation with NetSol against Cryptome which led to temporary closure back in February 2010. Microsoft withdrew its complaint over the publication of Redmond's spy guide for law enforcement after a campaign by techies.
A few months later a hacker group broke into Cryptome and erased its archive. Fortunately it was possible to rebuild the site from backups.
The planting of malicious code on Cryptome has happened before and had previously been handled by removing the malware without any interruption of service, according to Young.
Cryptome.org remains unavailable at the time of writing on Wednesday afternoon.
Disavowed
NetworkSolutions is owned by web.com. We've put in a query to web.com inviting it to say when Cryptome.org is likely to be restored as well as inviting it to comment of Young's criticism of its actions. We'll update this story as and when we hear back from the internet service firm.
Cryptome has been publishing leaked or otherwise sensitive documents since 1996. The site is particularly interested in material related to freedom of expression, privacy, cryptography, national security and intelligence but is by no means limited to those topics. ®
Update
Since the publication of this story, Web.com has been in touch with a statement. It said:
Network Solutions deactivated Cryptome.org due to security concerns with a potential malware threat. Our top priority is protecting the interest of our customers, and by extension, their customers. We are thoroughly investigating the situation and will have Cryptome.org back up and running as soon as is reasonably possible.
Meanwhile, the whistle-blowing site is saying that it plans to distribute its content in response to the site suspension.
Cryptome has been dispersed. Files will appear expectedly and unexpectedly at diverse locations online and off.
— Cryptome (@Cryptomeorg) June 25, 2014 